DIY Forth on Arduino
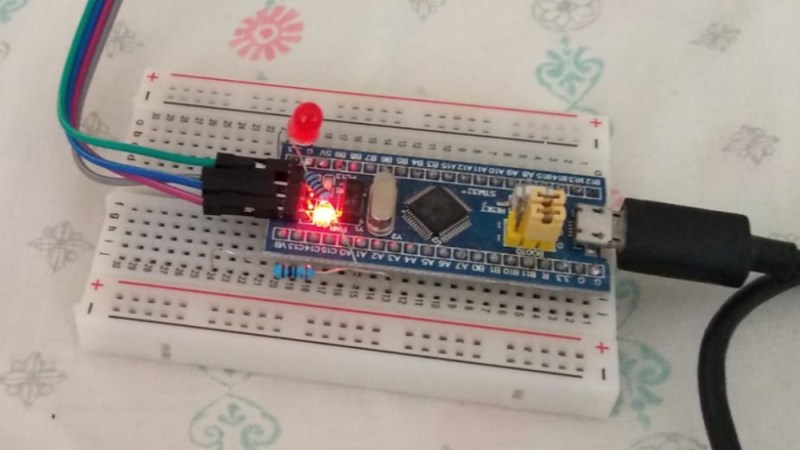
On a recent rainy afternoon, [Thanassis Tsiodras] decided to build his own Forth for the Arduino to relieve the boredom. One week of intense hacking later, he called it done …read more Continue reading DIY Forth on Arduino
Collaborate Disseminate

On a recent rainy afternoon, [Thanassis Tsiodras] decided to build his own Forth for the Arduino to relieve the boredom. One week of intense hacking later, he called it done …read more Continue reading DIY Forth on Arduino
In this blog series, I will be putting the spotlight on some useful Ghidra features you might have missed. Each post will look at a different feature and show how it helps you save time and be more effective in your reverse engineering workflows. Ghidr… Continue reading Ghidra 101: Decoding Stack Strings
TL;DR: We’re open-sourcing a new framework, blight, for painlessly wrapping and instrumenting C and C++ build tools. We’re already using it on our research projects, and have included a set of useful actions. You can use it today for your own measureme… Continue reading High-fidelity build instrumentation with blight
In 2020, our digital world and the software we use to create it are a towering structure, built upon countless layers of abstraction and building blocks — just think about all the translations and interactions that occur from loading a webpage. Whilst abstraction is undoubtedly a great thing, it only …read more
Continue reading Frances Allen Optimised Your Code Without You Even Knowing
Over the last few months, we’ve been fuzzing solc, the standard Solidity smart contract compiler, and we’ve racked up almost 20 (now mostly fixed) new bugs. A few of these are duplicates of existing bugs with slightly different symptoms or … Continue reading Breaking the Solidity Compiler with a Fuzzer
Zero-Day Snafus — Hunting Memory Allocation Bugs
Preface
Languages like C/C++ come with the whole “allocation party” of malloc, calloc, zalloc, realloc and their specialized versions kmalloc etc. For example, malloc has a… Continue reading Zero-Day Snafus — Hunting Memory Allocation Bugs
Each year, Trail of Bits runs a month-long winter internship aka “winternship” program. This year we were happy to host 4 winterns who contributed to 3 projects. This project comes from Carson Harmon, a new graduate from Purdue interested i… Continue reading Creating an LLVM Sanitizer from Hopes and Dreams
Trail of Bits has released Indurative, a cryptographic library that enables authentication of a wide variety of data structures without requiring users to write much code. Indurative is useful for everything from data integrity to trustless distributed… Continue reading Leaves of Hash
C++ programs using exceptions are problematic for binary lifters. The non-local control-flow “throw” and “catch” operations that appear in C++ source code do not map neatly to straightforward binary representations. One could al… Continue reading How McSema Handles C++ Exceptions
Today, we’re going to talk about a hard problem that we are working on as part of DARPA’s Cyber Fault-Tolerant Attack Recovery (CFAR) program: automatically protecting software from 0-day exploits, memory corruption, and many currently undi… Continue reading Protecting Software Against Exploitation with DARPA’s CFAR