No Privacy: Cloning the AirTag
You’ve probably heard of the infamous rule 34, but we’d like to propose a new rule — call it rule 35: Anything that can be used for nefarious purposes will …read more Continue reading No Privacy: Cloning the AirTag
Collaborate Disseminate

You’ve probably heard of the infamous rule 34, but we’d like to propose a new rule — call it rule 35: Anything that can be used for nefarious purposes will …read more Continue reading No Privacy: Cloning the AirTag

Even those readers who are most skeptical of Apple products will like this Bluetooth Low Energy (BLE)-enabled iOS app tutorial from [Akio]. With everything being “connected” these days smartphone applications …read more Continue reading Make Your Own BLE-Enabled iOS App From Scratch

Smartphones and voice assistants are the typical way most of us interact with our smart devices around the home, but it doesn’t have to be the only way. [Sam March] …read more Continue reading Turn On Your Lights With A Wave Of A Magic Wand
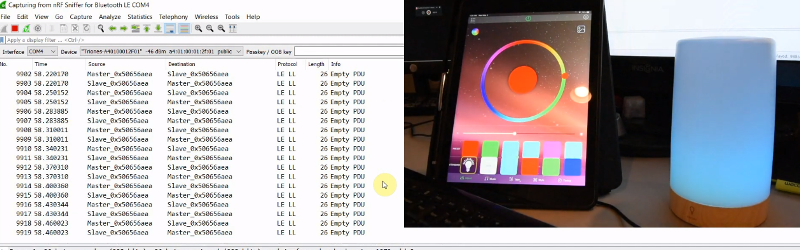
Bluetooth Low Energy (BLE) is everywhere these days. If you fire up a scanner on your phone and walk around the neighborhood, we’d be willing to bet you’d pick up …read more Continue reading A Crash Course on Sniffing Bluetooth Low Energy
Apple’s “Find My” service allows users to track their missing devices by leveraging a worldwide network of location-aware iGadgets. With millions of iPhones and Macs out in the wild listening for the missing device’s Bluetooth advertisements and relaying their findings …read more
Continue reading Get Apple to Track Your Bluetooth Devices For You
Terry Pratchett once said “Wisdom comes from experience. Experience is often a result of lack of wisdom.” This is as true with technical skills as it is with the rest of life, and you won’t truly understand a specific topic …read more
If we’ve learned anything over the years, it’s that hackers love to know what temperature it is. Seriously. A stroll through the archives here at Hackaday uncovers an overwhelming number of bespoke gadgets for recording, displaying, and transmitting the current conditions. From outdoor weather stations to an ESP8266 with a …read more
Continue reading Exploring Custom Firmware on Xiaomi Thermometers
Belgian researchers demonstrate third attack on the car manufacturer’s keyless entry system, this time to break into a Model X within minutes. Continue reading Tesla Hacked and Stolen Again Using Key Fob
The ‘BLESA’ flaw affects the reconnection process that occurs when a device moves back into range after losing or dropping its pairing, Purdue researchers said. Continue reading Bluetooth Spoofing Bug Affects Billions of IoT Devices
The “BLURtooth” flaw allows attackers within wireless range to bypass authentication keys and snoop on devices utilizing implementations of Bluetooth 4.0 through 5.0. Continue reading Bluetooth Bug Opens Devices to Man-in-the-Middle Attacks