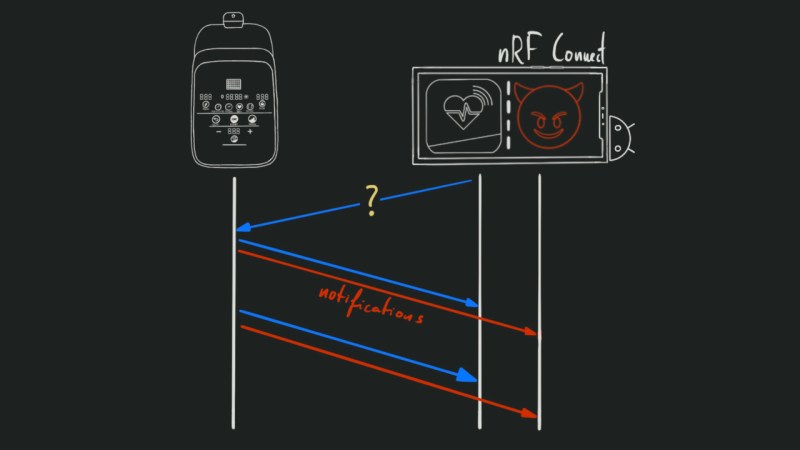
BSAM: Open-source methodology for Bluetooth security assessment
Many wireless headsets using Bluetooth technology have vulnerabilities that may allow malicious individuals to covertly listen in on private conversations, Tarlogic Security researchers have demonstrated last week at RootedCON in Madrid. “Many of… Continue reading BSAM: Open-source methodology for Bluetooth security assessment