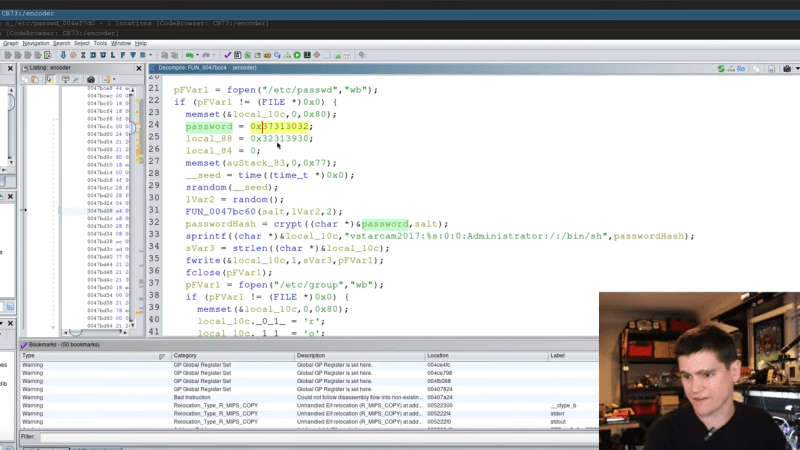
Cutting An IoT Fan Free Of The Cloud
The cloud is supposed to make everything better. You can control things remotely, with the aid of a benevolent corporation and their totally friendly servers. However, you might not like those servers, …read more Continue reading Cutting An IoT Fan Free Of The Cloud