Simple Antenna Makes for Better ESP32-C3 WiFi
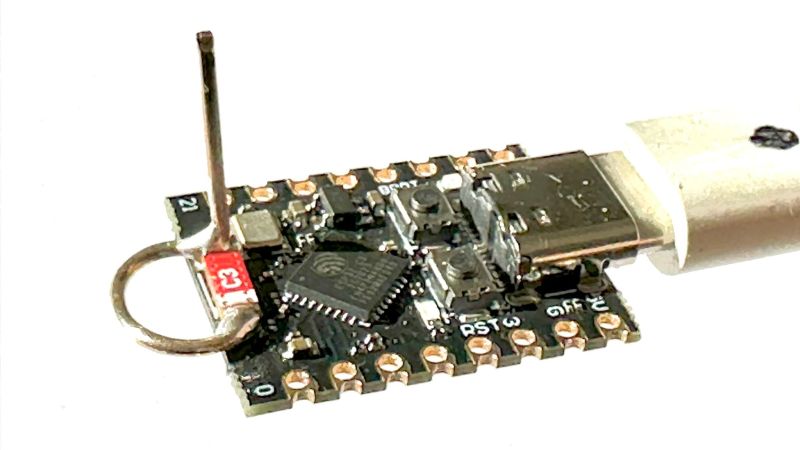
We’ve seen tons of projects lately using the ESP32-C3, and for good reason. The microcontroller has a lot to offer, and the current crop of tiny dev boards sporting it …read more Continue reading Simple Antenna Makes for Better ESP32-C3 WiFi

