Reverse Engineering a Topfield VFD Front Panel
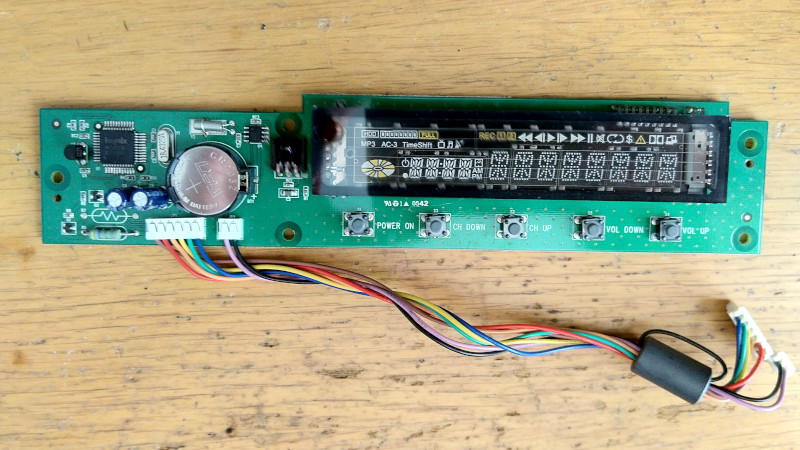
Hackers love the warm glow of a vacuum fluorescent display (VFD), and there’s no shortage of dead consumer electronics from which they can be pulled to keep our collective parts …read more Continue reading Reverse Engineering a Topfield VFD Front Panel