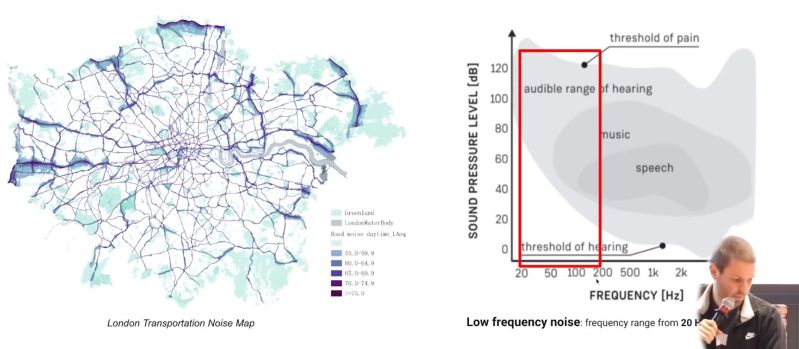
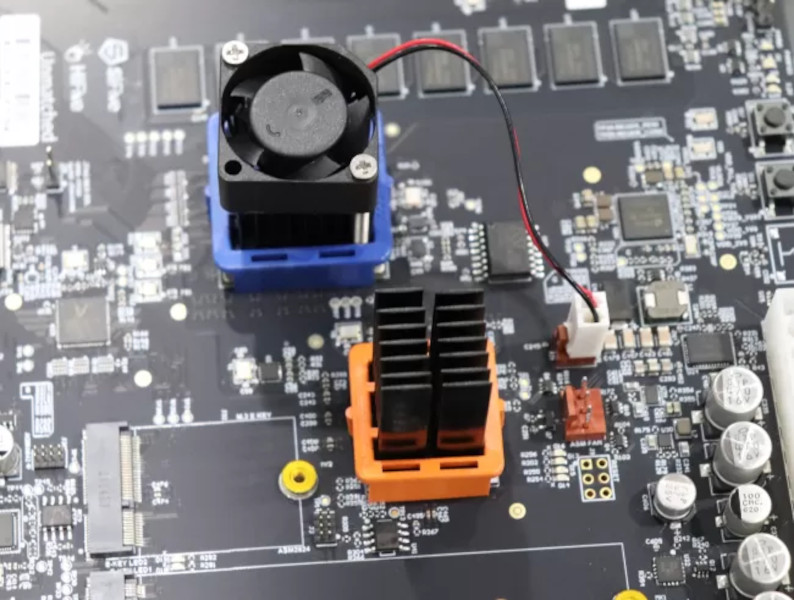
Hackaday Links: March 17, 2024

A friend of ours once described computers as “high-speed idiots.” It was true in the 80s, and it appears that even with the recent explosion in AI, all computers have …read more Continue reading Hackaday Links: March 17, 2024