7 million unsalted MD5 passwords leaked by Minecraft community Lifeboat
Worse still, service recommended “short, but difficult to guess passwords.” Continue reading 7 million unsalted MD5 passwords leaked by Minecraft community Lifeboat
Collaborate Disseminate
Worse still, service recommended “short, but difficult to guess passwords.” Continue reading 7 million unsalted MD5 passwords leaked by Minecraft community Lifeboat
Security researcher Troy Hunt obtained data containing email addresses and passwords hashed with the weak MD5 algorithm. Continue reading Another Day, Another Hack: 7 Million Accounts for Minecraft Community ‘Lifeboat’
I have a legacy system currently storing unsalted MD5 passwords. Unfortunately, some other controls are not in place (like the ability to expire passwords) and I’m trying to upgrade my algorithm to something newer and avoid prompting the … Continue reading Migrating password db off MD5 by chaining MD5 and Bcrypt?
All the examples of MD5 hash collisions I’ve come across comprise two different messages (inputs) of the same length. The first and second messages have different values for a number of bits and the resulting MD5’s are equal.
Does the theo… Continue reading Are there any known MD5 hash collisions of messages of different length?
Is there a way to actually find out whether a hash is MD5 or MD4?
For instance:
10c7ccc7a4f0aff03c915c485565b9da is an MD5 hash
be08c2de91787c51e7aee5dd16ca4f76 is an MD4 hash
I know that there is a difference “security… Continue reading Md5 vs Md4 recognition
I want to know whether it is possible to find out the salt of a MD5 hash?
For instance we’ve got two MD5 hashes
helloworld -> fc5e038d38a57032085441e7fe7010b0
goodbyeworld -> b34266c1c9eda200a0ebb833281bb855
Is it p… Continue reading Is it possible to find out the salt of a MD5 hash?
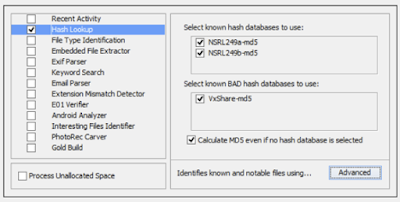 |
| Hash Lookup |
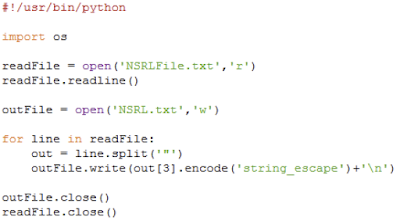 |
| NSRL Python Code |
 |
| Hash Lookup |
 |
| NSRL Python Code |
 |
| Hash Lookup |
 |
| NSRL Python Code |
I was just reading about SSL/TLS stuff, and according to this site (which is rated as A by Qualys SSL Labs), MD5 is totally broken, and SHA-1 is cryptographically weak since 2005. And yet, I noticed that a lot of programmers … Continue reading Why are MD5 and SHA-1 still used for checksums and certificates if they are called broken?