StaryDobry ruins New Year’s Eve, delivering miner instead of presents
StaryDobry campaign targets gamers with XMRig miner Continue reading StaryDobry ruins New Year’s Eve, delivering miner instead of presents
Collaborate Disseminate
StaryDobry campaign targets gamers with XMRig miner Continue reading StaryDobry ruins New Year’s Eve, delivering miner instead of presents
We analyze the latest activity by the Cloud Atlas gang. The attacks employ the PowerShower, VBShower and VBCloud modules to download victims’ data with various PowerShell scripts. Continue reading Cloud Atlas seen using a new tool in its attacks
Kaspersky experts describe an Elpaco ransomware sample, a Mimic variant, which abuses the Everything search system for Windows and provides custom features via a GUI. Continue reading Analysis of Elpaco: a Mimic variant
Kaspersky shares details on QSC modular cyberespionage framework, which appears to be linked to CloudComputating group campaigns. Continue reading QSC: A multi-plugin framework used by CloudComputating group in cyberespionage campaigns
Kaspersky experts have discovered a new version of the Loki agent for the open-source Mythic framework, which uses DLLs to attack Russian companies. Continue reading Loki: a new private agent for the popular Mythic framework
Kaspersky experts found a new variant of the China Chopper web shell from the Tropic Trooper group that imitates an Umbraco CMS module and targets a government entity in the Middle East. Continue reading Tropic Trooper spies on government entities in the Middle East
I published the following diary on isc.sans.edu: “Obscure Wininet.dll Feature?“: The Internet Storm Center relies on a group of Handlers who are volunteers and offer some free time to the community besides our daily job. Sometimes, we share information between us about an incident or a problem that we are facing and
The post [SANS ISC] Obscure Wininet.dll Feature? appeared first on /dev/random.
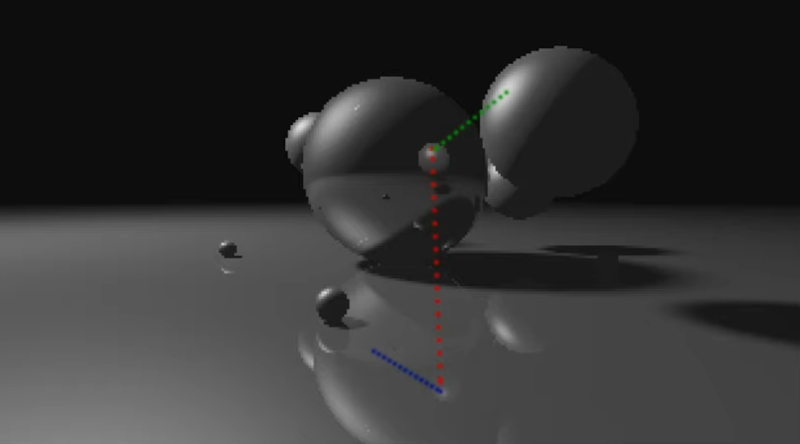
It isn’t news that [s0lly] likes to do ray tracing using Microsoft Excel. However, he recently updated his set up to use functions in a C XLL — a DLL, …read more Continue reading Excel Ray Tracing with Help from C
Recently, X-Force Red released a tool called Windows Feature Hunter, which identifies targets for dynamic link library (DLL) side-loading on a Windows system using Frida. To provide a defensive counter-measure perspective for DLL side-loading, X-Force Incident Response has released SideLoaderHunter, which is a system profiling script and Sysmon configuration designed to identify evidence of side-loading […]
The post Hunting for Evidence of DLL Side-Loading With PowerShell and Sysmon appeared first on Security Intelligence.
Continue reading Hunting for Evidence of DLL Side-Loading With PowerShell and Sysmon
I published the following diary on isc.sans.edu: “Locking Kernel32.dll As Anti-Debugging Technique“: For bad guys, the implementation of techniques to prevent Security Analysts to perform their job is key! The idea is to make our life more difficult (read: “frustrating”). There are plenty of techniques that can be implemented but
The post [SANS ISC] Locking Kernel32.dll As Anti-Debugging Technique appeared first on /dev/random.
Continue reading [SANS ISC] Locking Kernel32.dll As Anti-Debugging Technique