The ESP32 Doesn’t Need Much
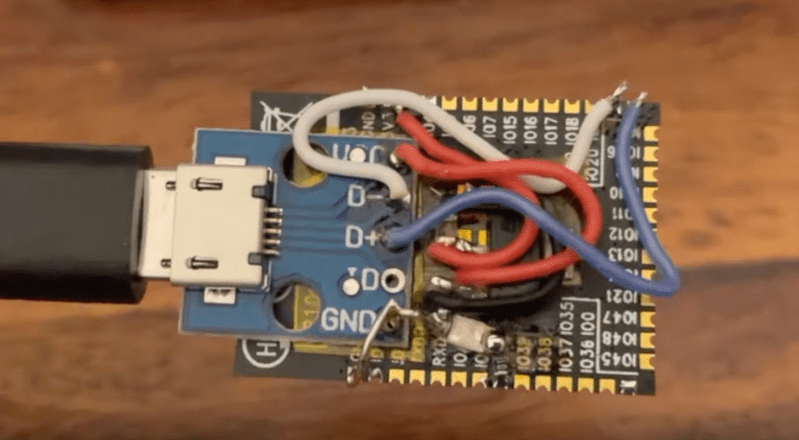
For those looking to add wireless connectivity to embedded projects or to build IoT devices, there is perhaps no more popular module than the ESP32. A dual-core option exists for …read more Continue reading The ESP32 Doesn’t Need Much
