Software Defined… CPU?
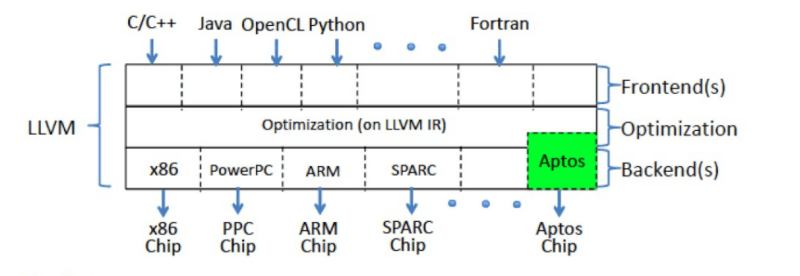
Everything is better when you can program it, right? We have software-defined radios, software-defined networks, and software-defined storage. Now a company called Ascenium wants to create a software-defined CPU. They’ve …read more Continue reading Software Defined… CPU?