APT trends report Q3 2024
The report features the most significant developments relating to APT groups in Q3 2024, including hacktivist activity, new APT tools and campaigns. Continue reading APT trends report Q3 2024
Collaborate Disseminate
The report features the most significant developments relating to APT groups in Q3 2024, including hacktivist activity, new APT tools and campaigns. Continue reading APT trends report Q3 2024
A "HID-compliant mouse" and a "USB composite device", both have no records in their "Device Manager – Properties – Events". Both are "currently not connected".
All other "Mice and other pointing… Continue reading A "HID-compliant mouse" and a "USB composite device", both have no records in their "Device Manager – Properties – Events" [migrated]
![[rasteri] holding his HIDMan USB dongle](https://hackaday.com/wp-content/uploads/2024/11/retro-usb-1200.jpg?w=800)
Retro computing enthusiasts, rejoice! HIDman, [rasteri]’s latest open source creation, bridges the gap between modern USB input devices and vintage PCs, from the IBM 5150 to machines with PS/2 ports. …read more Continue reading HIDman Brings Modern Input to Vintage PCs
Hackers can exploit critical vulnerabilities in Mazda’s infotainment system, including one that enables code execution via USB, compromising… Continue reading Hackers Can Access Mazda Vehicle Controls Via System Vulnerabilities
Goal:
I’m seeking feedback on the most secure setup for creating and accessing an encrypted database (KDBX4 format) that minimizes exposure to potential remote attacks. This database will contain highly sensitive information, and my primar… Continue reading Best Practice for Creating and Accessing an Encrypted Database with a Strong Threat Model
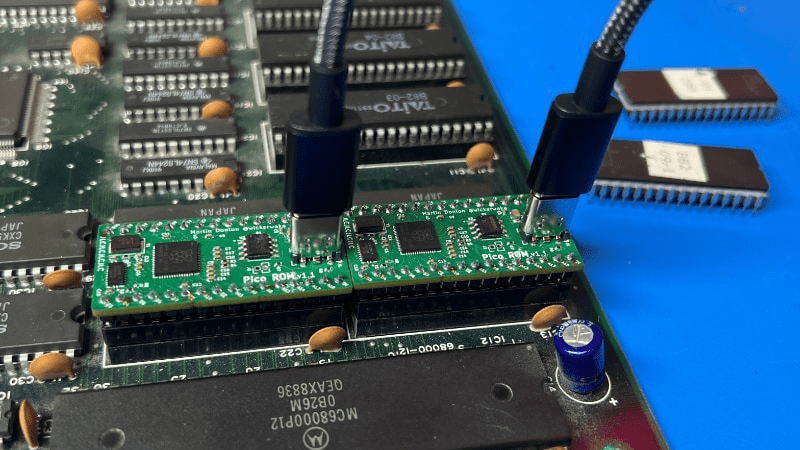
As we all know, when developing software for any platform or simply hacking a bit of code to probe how something works, the ability to deploy code rapidly is a …read more Continue reading PicoROM, A DIP-32 8-Bit ROM Emulator
USB 2 hubs are, by now, omnipresent. it doesn’t cost much to add to your board, and you truly have tons of options. The standard option is 4-port hubs – …read more Continue reading Ubiquitous Successful Bus: Hacking USB 2 Hubs
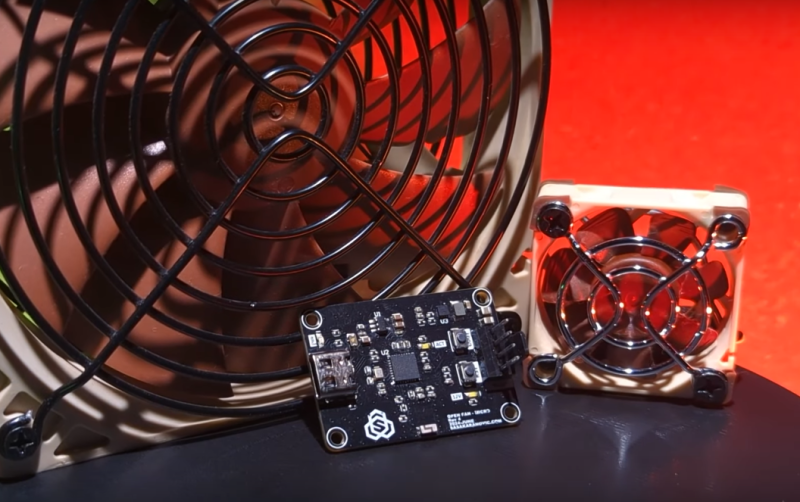
Most of us using desktop computers, and plenty of us on laptops, have some sort of fan or pump installed in our computer to remove heat and keep our machines …read more Continue reading Custom Fan Controller For Otherwise Fanless PCs
I had written an OS installation image to USB to be launched on untrusted PC. Can the untrusted PC modify USB’s installation image, for example Windows 10 image, so that when I plug in the same USB to another computer, it may rewrite the f… Continue reading Can USB installation stick rewrite any firmware inside my PC?
For network-based attacks, there are many tools that scan a system for open ports and perform fingerprinting to find out what software is running on the system.
Does something similar exist for USB ports that would detect available drivers… Continue reading "Scanning" available USB drivers on a port