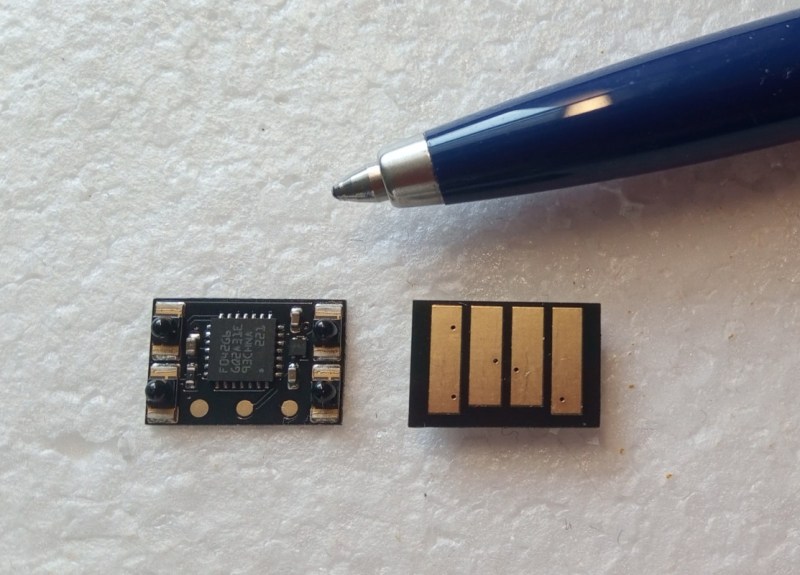
Piggyback Board Brings Touch Sensing to USB Soldering Iron

The current generation of USB-powered soldering irons have a lot going for them, chief among them being portability and automatic start and stop. But an iron that turns off in …read more Continue reading Piggyback Board Brings Touch Sensing to USB Soldering Iron