LCD Monitor Plays the Hits

In the old days, it wasn’t uncommon to put an AM radio near a computer or a monitor and deliberately cause interference to have a crude form of sound generation. …read more Continue reading LCD Monitor Plays the Hits
Collaborate Disseminate

In the old days, it wasn’t uncommon to put an AM radio near a computer or a monitor and deliberately cause interference to have a crude form of sound generation. …read more Continue reading LCD Monitor Plays the Hits
If you ever get the feeling someone is watching you, maybe they are listening, too. At least they might be listening to what’s coming over your computer speakers thanks to …read more Continue reading Eavesdropping by LED
Since the ether is an old term for the fictitious space where radio waves propagate, we always thought it was strange that the term ethernet refers to wired communication. Sure, there are wireless devices, but that’s not really ethernet. [Jacek] had the same thought, but decided to do something about …read more
Electronic devices can be surprisingly leaky, often spraying out information for anyone close by to receive. [Docter Cube] has found another such leak, this time with the speakers in iPhones. While repairing an old AM radio and listening to a podcast on his iPhone, he discovered that the radio was …read more
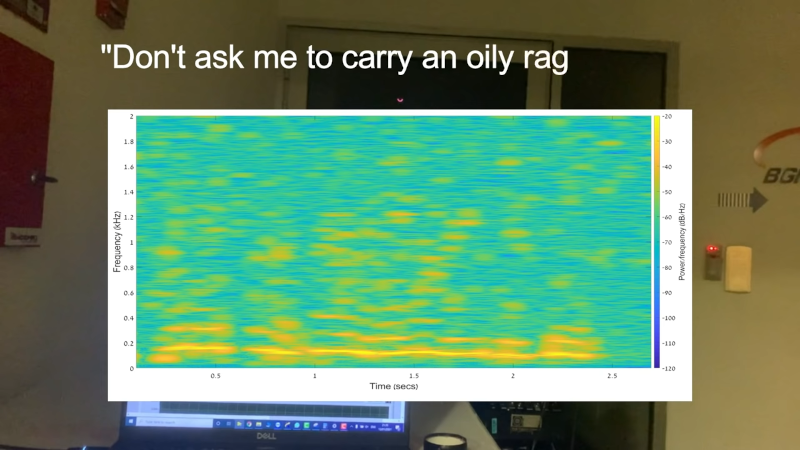
As we use our computers, to watch YouTube videos of trucks hitting bridges, to have a Zoom call with our mothers, or even for some of us to write Hackaday articles, we’re unknowingly sharing a lot of what we are doing with the world. The RF emissions from our monitors, …read more
A researcher has figured out how to get a PC’s power supply to make noises. Why’s that interesting? Because it could be used to transmit data.
The post Steal Data Though Sound, Sans Speaker? appeared first on Security Boulevard.
Continue reading Steal Data Though Sound, Sans Speaker?
Tom’s Guide writes about home brew TEMPEST receivers: Today, dirt-cheap technology and free software make it possible for ordinary citizens to run their own Tempest programs and listen to what their own — and their neighbors’ — electronic devices are doing. Elliott, a researcher at Boston-based security company Veracode, showed that an inexpensive USB dongle TV tuner costing about $10… Continue reading Homemade TEMPEST Receiver
As long as there has been radio, people have wanted to eavesdrop on radio transmissions. In many cases, it is just a hobby activity like listening to a scanner or monitoring a local repeater. But in some cases, it is spy agencies or cyberhackers. [Giovanni Camurati] and his colleagues have been working on a slightly different way to attack Bluetooth radio communications using a technique that could apply to other radio types, too. The attack relies on the ubiquitous use of mixed-signal ICs to make cheap radios like Bluetooth dongles. They call it “Screaming Channels” and — in a nutshell …read more
In 1985, [Wim van Eck] published several technical reports on obtaining information the electromagnetic emissions of computer systems. In one analysis, [van Eck] reliably obtained data from a computer system over hundreds of meters using just a handful of components and a TV set. There were obvious security implications, and now computer systems handling highly classified data are TEMPEST shielded – an NSA specification for protection from this van Eck phreaking.
Methods of van Eck phreaking are as numerous as they are awesome. [Craig Ramsay] at Fox It has demonstrated a new method of this interesting side-channel analysis using readily …read more
It is incredibly interesting how many parts of a computer system are capable of leaking data in ways that is hard to imaging. Part of securing highly sensitive locations involves securing the computers and networks used in those facilities in order to prevent this. These IT security policies and practices have been evolving and tightening through the years, as malicious actors increasingly target vital infrastructure.
Sometimes, when implementing strong security measures on a vital computer system, a technique called air-gapping is used. Air-gapping is a measure or set of measures to ensure a secure computer is physically isolated from unsecured …read more
![]() Continue reading Hacking the Aether: How Data Crosses the Air-Gap
Continue reading Hacking the Aether: How Data Crosses the Air-Gap