Photoresistors Provide Air Gap Data Transfer, Slowly
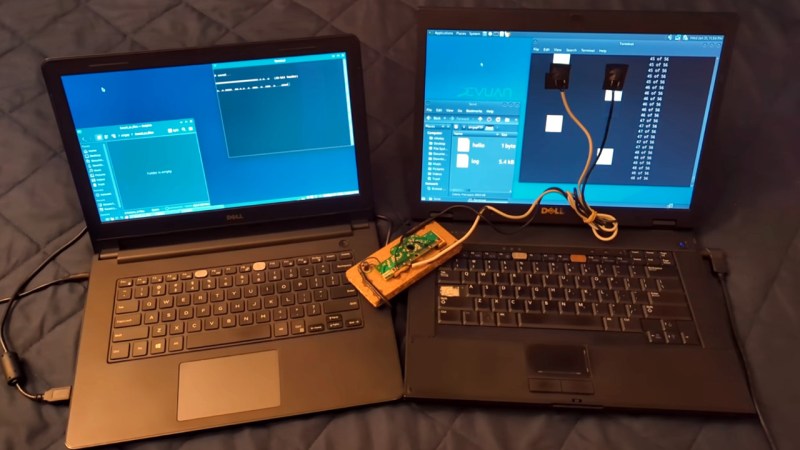
One of the simplest ways of keeping a computer system secure is by using an air gap — that is, never actually connecting the system to the network. This can …read more Continue reading Photoresistors Provide Air Gap Data Transfer, Slowly
