KolibriOS: The Operating System That Fits on a 1.44 MB 3.5″ Floppy Disk
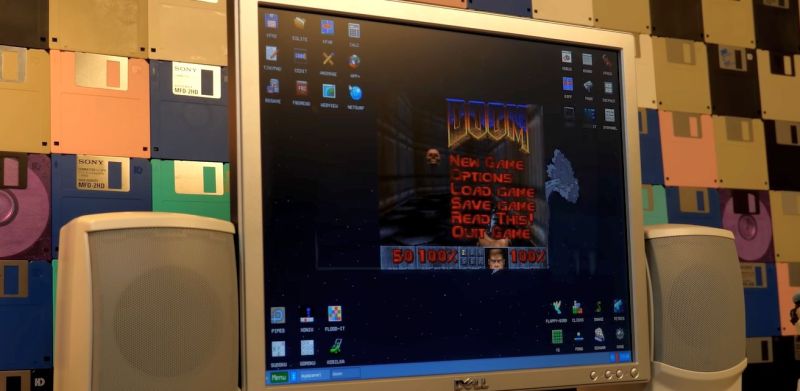
While most operating systems are written in C and C++, KolibriOS is written in pure x86 assembly and as a result small and lightweight enough to run off a standard …read more Continue reading KolibriOS: The Operating System That Fits on a 1.44 MB 3.5″ Floppy Disk
