Hands-On With PineCube: An Open IP Camera Begging for Better Kernel Support
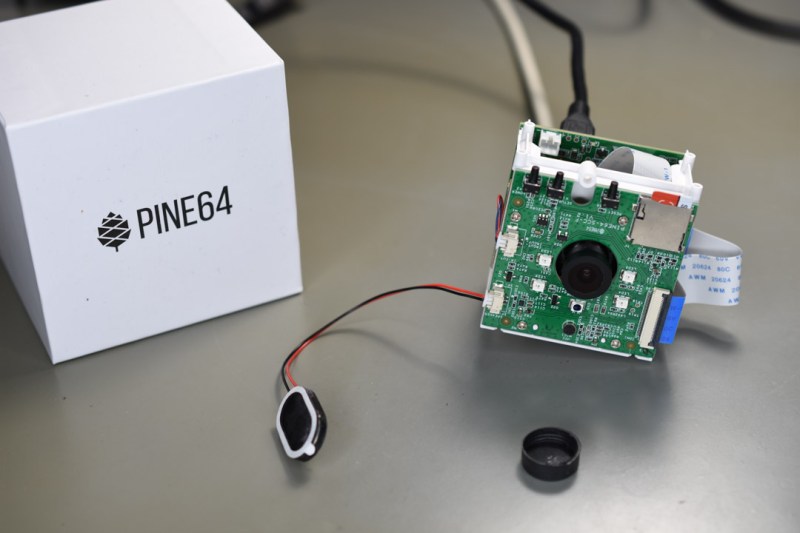
When the PineCube was announced by the Pine64 project in 2020, it created a fair bit of interest. Most of this was due to the appeal of a single-board computer …read more Continue reading Hands-On With PineCube: An Open IP Camera Begging for Better Kernel Support