An Overly Complicated Method of Tracking Your Favorite Sports Team
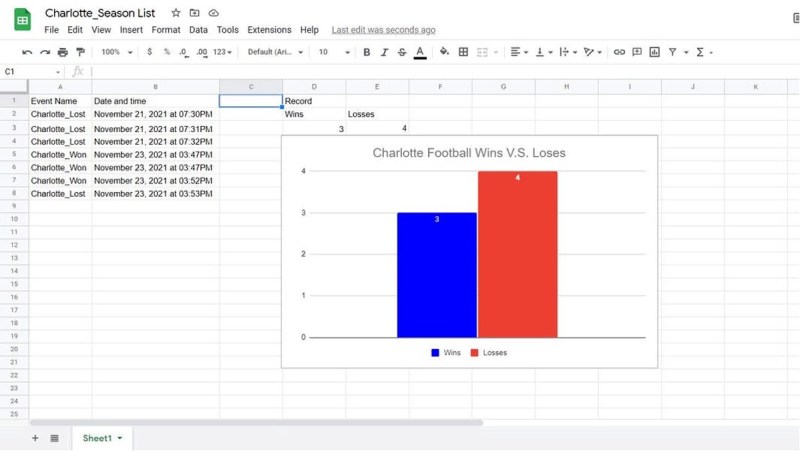
Much of the world appears to revolve around sports, and sports tracking is a pretty big business. So how do people keep up with their favorite team? Well, [Jackson] and …read more Continue reading An Overly Complicated Method of Tracking Your Favorite Sports Team