Most Hunt Management Plans Aren’t Based in Science
In a new study, 60 percent of plans—spanning Canadian provinces and US states—lacked a scientific approach. Continue reading Most Hunt Management Plans Aren’t Based in Science
Collaborate Disseminate
In a new study, 60 percent of plans—spanning Canadian provinces and US states—lacked a scientific approach. Continue reading Most Hunt Management Plans Aren’t Based in Science
As we celebrate Independence Day, I’m reminded that we honor what was, of course, an armed conflict. Today’s realities, when we think about conflict, are quite different that the days of lining troops up across the field from each other, loading musket… Continue reading Toolsmith #126: Adversary hunting with SOF-ELK
As we celebrate Independence Day, I’m reminded that we honor what was, of course, an armed conflict. Today’s realities, when we think about conflict, are quite different than the days of lining troops up across the field from each other, loading musket… Continue reading Toolsmith #126: Adversary hunting with SOF-ELK
Some Indigenous communities rely on the caribou hunt. Continue reading The Arctic Is Getting Greener But Its Caribou Are Dying
As you weigh how best to improve your organization’s digital forensics and incident response (DFIR) capabilities heading into 2017, consider Matt Swann‘s Incident Response Hierarchy of Needs. Likely, at some point in your career (or therapy 
Matt has made great use of this model to describe an Incident Response Hierarchy of Needs, through which your DFIR methods should move. I argue that his powerful description of capabilities extends to the whole of DFIR rather than response alone. From Matt’s Github, “the Incident Response Hierarchy describes the capabilities that organizations must build to defend their business assets. Bottom capabilities are prerequisites for successful execution of the capabilities above them:”
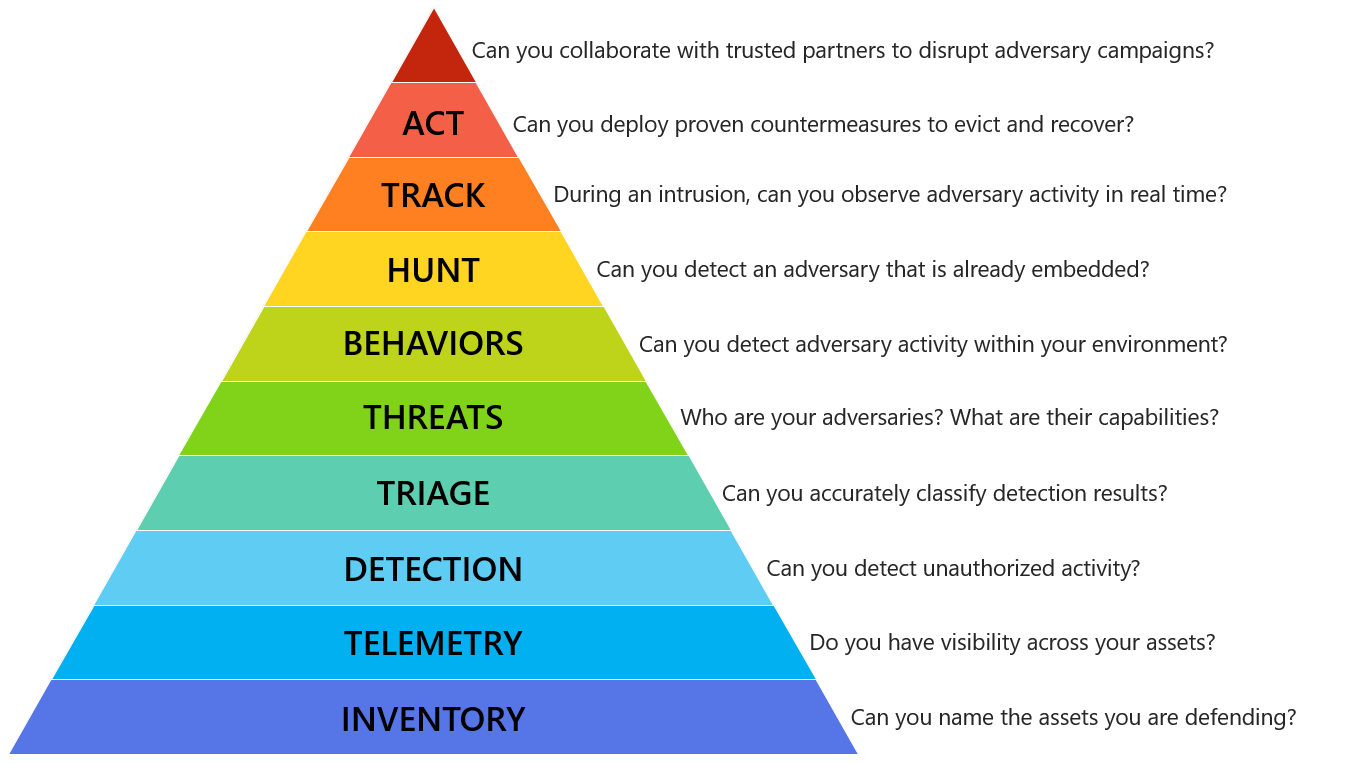 |
|||||||||
| The Incident Response Hierarchy of Needs |
“The capabilities may also be organized into plateaus or phases that organizations may experience as they develop these capabilities:”
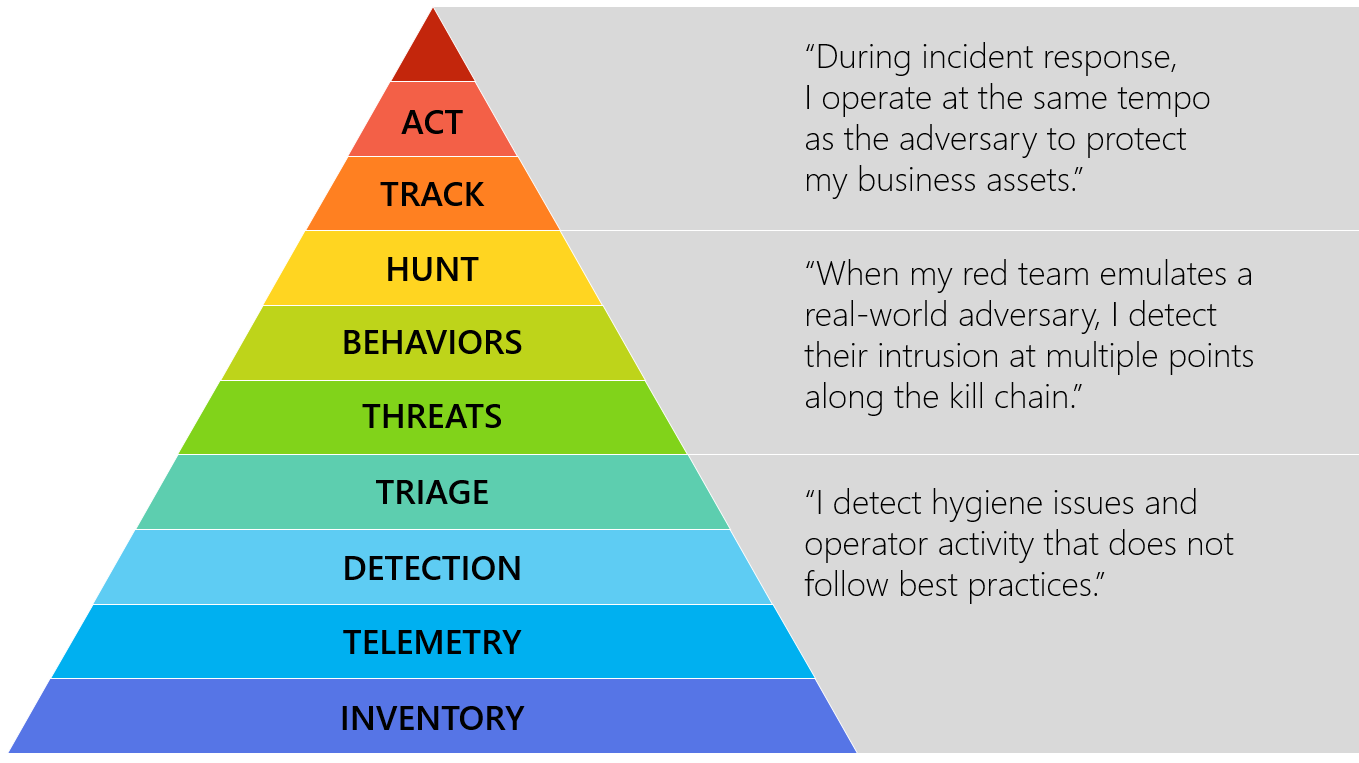 |
| Hierarchy plateaus or phases |
As visualizations, these representations really do speak for themselves, and I applaud Matt’s fine work. I would like to propose that a body of references and controls may be of use to you in achieving this hierarchy to its utmost. I also welcome your feedback and contributions regarding how to achieve each of these needs and phases. Feel free to submit controls, tools, and tactics you have or would deploy to be successful in these endeavors; I’ll post your submission along with your preferred social media handle.
Aspects of the Center for Internet Security Critical Security Controls Version 6.1 (CIS CSC) can be mapped to each of Matt’s hierarchical entities and phases. Below I offer one control and one tool to support each entry. Note that there is a level of subjectivity to these mappings and tooling, but the intent is to help you adopt this thinking and achieve this agenda. Following is an example for each one, starting from the bottom of the pyramid.
INVENTORY – Can you name the assets you are defending?
Critical Security Control #1: Inventory of Authorized and Unauthorized Devices
Family: System
Control: 1.4
“Maintain an asset inventory of all systems connected to the network and the network devices themselves, recording at least the network addresses, machine name(s), purpose of each system, an asset owner responsible for each device, and the department associated with each device. The inventory should include every system that has an Internet protocol (IP) address on the network, including but not limited to desktops, laptops, servers, network equipment (routers, switches, firewalls, etc.), printers, storage area networks, Voice Over-IP telephones, multi-homed addresses, virtual addresses, etc. The asset inventory created must also include data on whether the device is a portable and/or personal device. Devices such as mobile phones, tablets, laptops, and other portable electronic devices that store or process data must be identified, regardless of whether they are attached to the organization’s network.”
Tool option:
Spiceworks Inventory
TELEMETRY – Do you have visibility across your assets?
Critical Security Control #6: Maintenance, Monitoring, and Analysis of Audit Logs
Family: System
Control: 6.6 “Deploy a SIEM (Security Information and Event Management) or log analytic tools for log aggregation and consolidation from multiple machines and for log correlation and analysis. Using the SIEM tool, system administrators and security personnel should devise profiles of common events from given systems so that they can tune detection to focus on unusual activity, avoid false positives, more rapidly identify anomalies, and prevent overwhelming analysts with insignificant alerts.”
Tool option:
AlienVault OSSIM
DETECTION – Can you detect unauthorized actvity?
Critical Security Control #8: Malware Defenses
Family: System
Control: 8.1
“Employ automated tools to continuously monitor workstations, servers, and mobile devices with anti-virus, anti-spyware, personal firewalls, and host-based IPS functionality. All malware detection events should be sent to enterprise anti-malware administration tools and event log servers.”
Tool option:
OSSEC Open Source HIDS SECurity
TRIAGE – Can you accurately classify detection results?
Critical Security Control #4: Continuous Vulnerability Assessment and Remediation
Family: System
Control: 4.3
“Correlate event logs with information from vulnerability scans to fulfill two goals. First, personnel should verify that the activity of the regular vulnerability scanning tools is itself logged. Second, personnel should be able to correlate attack detection events with prior vulnerability scanning results to determine whether the given exploit was used against a target known to be vulnerable.”
Tool option:
OpenVAS
THREATS – Who are your adversaries? What are their capabilities?
Critical Security Control #19: Incident Response and Management
Family: Application
Control: 19.7
“Conduct periodic incident scenario sessions for personnel associated with the incident handling team to ensure that they understand current threats and risks, as well as their responsibilities in supporting the incident handling team.”
Tool option:
Security Incident Response Testing To Meet Audit Requirements
BEHAVIORS – Can you detect adversary activity within your environment?
Critical Security Control #5: Controlled Use of Administrative Privileges
Family: System
Control: 5.1
“Minimize administrative privileges and only use administrative accounts when they are required. Implement focused auditing on the use of administrative privileged functions and monitor for anomalous behavior.”
Tool option:
Local Administrator Password Solution (LAPS)
HUNT – Can you detect an adversary that is already embedded?
Critical Security Control #6: Maintenance, Monitoring, and Analysis of Audit Logs
Family: System
Control: 6.4
“Have security personnel and/or system administrators run biweekly reports that identify anomalies in logs. They should then actively review the anomalies, documenting their findings.”
Tool option:
GRR Rapid Response
TRACK – During an intrusion, can you observe adversary activity in real time?
Critical Security Control #12: Boundary Defense
Family: Network
Control: 12.10
“To help identify covert channels exfiltrating data through a firewall, configure the built-in firewall session tracking mechanisms included in many commercial firewalls to identify TCP sessions that last an unusually long time for the given organization and firewall device, alerting personnel about the source and destination addresses associated with these long sessions.”
Tool option:
Bro
ACT – Can you deploy countermeasures to evict and recover?
Critical Security Control #20: Penetration Tests and Red Team Exercises
Family: Application
Control: 20.3
“Perform periodic Red Team exercises to test organizational readiness to identify and stop attacks or to respond quickly and effectively.”
Tool option:
Red vs Blue – PowerSploit vs PowerForensics
Can you collaborate with trusted parties to disrupt adversary campaigns?
Critical Security Control #19: Incident Response and Management
Family: Application
Control: 19.5
“Assemble and maintain information on third-party contact information to be used to report a security incident (e.g., maintain an e-mail address of security@organization.com or have a web page http://organization.com/security).”
Tool option:
MISP
I’ve also started to map the hierarchy to the controls in CIS CSC 6.1 spreadsheet, again based on my experience and perspective, your may differ, but consider similar activity.
I’ll make my first pass at the spreadsheet mapping effort available here shortly.
I truly hope you familiarize yourself with Matt‘s Incident Response Hierarchy of Needs and find ways to implement, validate, and improve your capabilities accordingly. Consider that the controls and tools mentioned here are but a starting point and that you have many other options available to you. I look forward to hearing from you regarding your preferred tactics and tools as well. Kudos to Matt for framing this essential discussion so distinctly.
Continue reading The DFIR Hierarchy of Needs & Critical Security Controls
As you weigh how best to improve your organization’s digital forensics and incident response (DFIR) capabilities heading into 2017, consider Matt Swann‘s Incident Response Hierarchy of Needs. Likely, at some point in your career (or therapy 
Matt has made great use of this model to describe an Incident Response Hierarchy of Needs, through which your DFIR methods should move. I argue that his powerful description of capabilities extends to the whole of DFIR rather than response alone. From Matt’s Github, “the Incident Response Hierarchy describes the capabilities that organizations must build to defend their business assets. Bottom capabilities are prerequisites for successful execution of the capabilities above them:”
 |
|||||||||
| The Incident Response Hierarchy of Needs |
“The capabilities may also be organized into plateaus or phases that organizations may experience as they develop these capabilities:”
 |
| Hierarchy plateaus or phases |
As visualizations, these representations really do speak for themselves, and I applaud Matt’s fine work. I would like to propose that a body of references and controls may be of use to you in achieving this hierarchy to its utmost. I also welcome your feedback and contributions regarding how to achieve each of these needs and phases. Feel free to submit controls, tools, and tactics you have or would deploy to be successful in these endeavors; I’ll post your submission along with your preferred social media handle.
Aspects of the Center for Internet Security Critical Security Controls Version 6.1 (CIS CSC) can be mapped to each of Matt’s hierarchical entities and phases. Below I offer one control and one tool to support each entry. Note that there is a level of subjectivity to these mappings and tooling, but the intent is to help you adopt this thinking and achieve this agenda. Following is an example for each one, starting from the bottom of the pyramid.
INVENTORY – Can you name the assets you are defending?
Critical Security Control #1: Inventory of Authorized and Unauthorized Devices
Family: System
Control: 1.4
“Maintain an asset inventory of all systems connected to the network and the network devices themselves, recording at least the network addresses, machine name(s), purpose of each system, an asset owner responsible for each device, and the department associated with each device. The inventory should include every system that has an Internet protocol (IP) address on the network, including but not limited to desktops, laptops, servers, network equipment (routers, switches, firewalls, etc.), printers, storage area networks, Voice Over-IP telephones, multi-homed addresses, virtual addresses, etc. The asset inventory created must also include data on whether the device is a portable and/or personal device. Devices such as mobile phones, tablets, laptops, and other portable electronic devices that store or process data must be identified, regardless of whether they are attached to the organization’s network.”
Tool option:
Spiceworks Inventory
TELEMETRY – Do you have visibility across your assets?
Critical Security Control #6: Maintenance, Monitoring, and Analysis of Audit Logs
Family: System
Control: 6.6 “Deploy a SIEM (Security Information and Event Management) or log analytic tools for log aggregation and consolidation from multiple machines and for log correlation and analysis. Using the SIEM tool, system administrators and security personnel should devise profiles of common events from given systems so that they can tune detection to focus on unusual activity, avoid false positives, more rapidly identify anomalies, and prevent overwhelming analysts with insignificant alerts.”
Tool option:
AlienVault OSSIM
DETECTION – Can you detect unauthorized actvity?
Critical Security Control #8: Malware Defenses
Family: System
Control: 8.1
“Employ automated tools to continuously monitor workstations, servers, and mobile devices with anti-virus, anti-spyware, personal firewalls, and host-based IPS functionality. All malware detection events should be sent to enterprise anti-malware administration tools and event log servers.”
Tool option:
OSSEC Open Source HIDS SECurity
TRIAGE – Can you accurately classify detection results?
Critical Security Control #4: Continuous Vulnerability Assessment and Remediation
Family: System
Control: 4.3
“Correlate event logs with information from vulnerability scans to fulfill two goals. First, personnel should verify that the activity of the regular vulnerability scanning tools is itself logged. Second, personnel should be able to correlate attack detection events with prior vulnerability scanning results to determine whether the given exploit was used against a target known to be vulnerable.”
Tool option:
OpenVAS
THREATS – Who are your adversaries? What are their capabilities?
Critical Security Control #19: Incident Response and Management
Family: Application
Control: 19.7
“Conduct periodic incident scenario sessions for personnel associated with the incident handling team to ensure that they understand current threats and risks, as well as their responsibilities in supporting the incident handling team.”
Tool option:
Security Incident Response Testing To Meet Audit Requirements
BEHAVIORS – Can you detect adversary activity within your environment?
Critical Security Control #5: Controlled Use of Administrative Privileges
Family: System
Control: 5.1
“Minimize administrative privileges and only use administrative accounts when they are required. Implement focused auditing on the use of administrative privileged functions and monitor for anomalous behavior.”
Tool option:
Local Administrator Password Solution (LAPS)
HUNT – Can you detect an adversary that is already embedded?
Critical Security Control #6: Maintenance, Monitoring, and Analysis of Audit Logs
Family: System
Control: 6.4
“Have security personnel and/or system administrators run biweekly reports that identify anomalies in logs. They should then actively review the anomalies, documenting their findings.”
Tool option:
GRR Rapid Response
TRACK – During an intrusion, can you observe adversary activity in real time?
Critical Security Control #12: Boundary Defense
Family: Network
Control: 12.10
“To help identify covert channels exfiltrating data through a firewall, configure the built-in firewall session tracking mechanisms included in many commercial firewalls to identify TCP sessions that last an unusually long time for the given organization and firewall device, alerting personnel about the source and destination addresses associated with these long sessions.”
Tool option:
Bro
ACT – Can you deploy countermeasures to evict and recover?
Critical Security Control #20: Penetration Tests and Red Team Exercises
Family: Application
Control: 20.3
“Perform periodic Red Team exercises to test organizational readiness to identify and stop attacks or to respond quickly and effectively.”
Tool option:
Red vs Blue – PowerSploit vs PowerForensics
Can you collaborate with trusted parties to disrupt adversary campaigns?
Critical Security Control #19: Incident Response and Management
Family: Application
Control: 19.5
“Assemble and maintain information on third-party contact information to be used to report a security incident (e.g., maintain an e-mail address of security@organization.com or have a web page http://organization.com/security).”
Tool option:
MISP
I’ve mapped the hierarchy to the controls in CIS CSC 6.1 spreadsheet, again based on my experience and perspective, yours may differ, but consider similar activity.
 |
| CIS CSC with IR Hierarchy mappings |
My full mapping of Matt’s Incident Response Hierarchy of Needs in the
CIS CSC 6.1 spreadsheet is available here: http://bit.ly/CSC-IRH
I truly hope you familiarize yourself with Matt‘s Incident Response Hierarchy of Needs and find ways to implement, validate, and improve your capabilities accordingly. Consider that the controls and tools mentioned here are but a starting point and that you have many other options available to you. I look forward to hearing from you regarding your preferred tactics and tools as well. Kudos to Matt for framing this essential discussion so distinctly.
Continue reading The DFIR Hierarchy of Needs & Critical Security Controls
As you weigh how best to improve your organization’s digital forensics and incident response (DFIR) capabilities heading into 2017, consider Matt Swann‘s Incident Response Hierarchy of Needs. Likely, at some point in your career (or therapy 
Matt has made great use of this model to describe an Incident Response Hierarchy of Needs, through which your DFIR methods should move. I argue that his powerful description of capabilities extends to the whole of DFIR rather than response alone. From Matt’s Github, “the Incident Response Hierarchy describes the capabilities that organizations must build to defend their business assets. Bottom capabilities are prerequisites for successful execution of the capabilities above them:”
 |
|||||||||
| The Incident Response Hierarchy of Needs |
“The capabilities may also be organized into plateaus or phases that organizations may experience as they develop these capabilities:”
 |
| Hierarchy plateaus or phases |
As visualizations, these representations really do speak for themselves, and I applaud Matt’s fine work. I would like to propose that a body of references and controls may be of use to you in achieving this hierarchy to its utmost. I also welcome your feedback and contributions regarding how to achieve each of these needs and phases. Feel free to submit controls, tools, and tactics you have or would deploy to be successful in these endeavors; I’ll post your submission along with your preferred social media handle.
Aspects of the Center for Internet Security Critical Security Controls Version 6.1 (CIS CSC) can be mapped to each of Matt’s hierarchical entities and phases. Below I offer one control and one tool to support each entry. Note that there is a level of subjectivity to these mappings and tooling, but the intent is to help you adopt this thinking and achieve this agenda. Following is an example for each one, starting from the bottom of the pyramid.
INVENTORY – Can you name the assets you are defending?
Critical Security Control #1: Inventory of Authorized and Unauthorized Devices
Family: System
Control: 1.4
“Maintain an asset inventory of all systems connected to the network and the network devices themselves, recording at least the network addresses, machine name(s), purpose of each system, an asset owner responsible for each device, and the department associated with each device. The inventory should include every system that has an Internet protocol (IP) address on the network, including but not limited to desktops, laptops, servers, network equipment (routers, switches, firewalls, etc.), printers, storage area networks, Voice Over-IP telephones, multi-homed addresses, virtual addresses, etc. The asset inventory created must also include data on whether the device is a portable and/or personal device. Devices such as mobile phones, tablets, laptops, and other portable electronic devices that store or process data must be identified, regardless of whether they are attached to the organization’s network.”
Tool option:
Spiceworks Inventory
TELEMETRY – Do you have visibility across your assets?
Critical Security Control #6: Maintenance, Monitoring, and Analysis of Audit Logs
Family: System
Control: 6.6 “Deploy a SIEM (Security Information and Event Management) or log analytic tools for log aggregation and consolidation from multiple machines and for log correlation and analysis. Using the SIEM tool, system administrators and security personnel should devise profiles of common events from given systems so that they can tune detection to focus on unusual activity, avoid false positives, more rapidly identify anomalies, and prevent overwhelming analysts with insignificant alerts.”
Tool option:
AlienVault OSSIM
DETECTION – Can you detect unauthorized actvity?
Critical Security Control #8: Malware Defenses
Family: System
Control: 8.1
“Employ automated tools to continuously monitor workstations, servers, and mobile devices with anti-virus, anti-spyware, personal firewalls, and host-based IPS functionality. All malware detection events should be sent to enterprise anti-malware administration tools and event log servers.”
Tool option:
OSSEC Open Source HIDS SECurity
TRIAGE – Can you accurately classify detection results?
Critical Security Control #4: Continuous Vulnerability Assessment and Remediation
Family: System
Control: 4.3
“Correlate event logs with information from vulnerability scans to fulfill two goals. First, personnel should verify that the activity of the regular vulnerability scanning tools is itself logged. Second, personnel should be able to correlate attack detection events with prior vulnerability scanning results to determine whether the given exploit was used against a target known to be vulnerable.”
Tool option:
OpenVAS
THREATS – Who are your adversaries? What are their capabilities?
Critical Security Control #19: Incident Response and Management
Family: Application
Control: 19.7
“Conduct periodic incident scenario sessions for personnel associated with the incident handling team to ensure that they understand current threats and risks, as well as their responsibilities in supporting the incident handling team.”
Tool option:
Security Incident Response Testing To Meet Audit Requirements
BEHAVIORS – Can you detect adversary activity within your environment?
Critical Security Control #5: Controlled Use of Administrative Privileges
Family: System
Control: 5.1
“Minimize administrative privileges and only use administrative accounts when they are required. Implement focused auditing on the use of administrative privileged functions and monitor for anomalous behavior.”
Tool option:
Local Administrator Password Solution (LAPS)
HUNT – Can you detect an adversary that is already embedded?
Critical Security Control #6: Maintenance, Monitoring, and Analysis of Audit Logs
Family: System
Control: 6.4
“Have security personnel and/or system administrators run biweekly reports that identify anomalies in logs. They should then actively review the anomalies, documenting their findings.”
Tool option:
GRR Rapid Response
TRACK – During an intrusion, can you observe adversary activity in real time?
Critical Security Control #12: Boundary Defense
Family: Network
Control: 12.10
“To help identify covert channels exfiltrating data through a firewall, configure the built-in firewall session tracking mechanisms included in many commercial firewalls to identify TCP sessions that last an unusually long time for the given organization and firewall device, alerting personnel about the source and destination addresses associated with these long sessions.”
Tool option:
Bro
ACT – Can you deploy countermeasures to evict and recover?
Critical Security Control #20: Penetration Tests and Red Team Exercises
Family: Application
Control: 20.3
“Perform periodic Red Team exercises to test organizational readiness to identify and stop attacks or to respond quickly and effectively.”
Tool option:
Red vs Blue – PowerSploit vs PowerForensics
Can you collaborate with trusted parties to disrupt adversary campaigns?
Critical Security Control #19: Incident Response and Management
Family: Application
Control: 19.5
“Assemble and maintain information on third-party contact information to be used to report a security incident (e.g., maintain an e-mail address of security@organization.com or have a web page http://organization.com/security).”
Tool option:
MISP
I’ve mapped the hierarchy to the controls in CIS CSC 6.1 spreadsheet, again based on my experience and perspective, yours may differ, but consider similar activity.
 |
| CIS CSC with IR Hierarchy mappings |
My full mapping of Matt’s Incident Response Hierarchy of Needs in the
CIS CSC 6.1 spreadsheet is available here: http://bit.ly/CSC-IRH
I truly hope you familiarize yourself with Matt‘s Incident Response Hierarchy of Needs and find ways to implement, validate, and improve your capabilities accordingly. Consider that the controls and tools mentioned here are but a starting point and that you have many other options available to you. I look forward to hearing from you regarding your preferred tactics and tools as well. Kudos to Matt for framing this essential discussion so distinctly.
Continue reading The DFIR Hierarchy of Needs & Critical Security Controls
We benefit this month from another offering first spotted via my fellow tool aficionados over at Toolswatch. And just like that, bam! A Beatles song…stuck in my head…all day.The crazy crew at Blackhills Security have embarked on another cool project: Real Intelligence Threat Analysis, or RITA, thus named because “Johns’ mom” was already taken.
 |
Yep, that kind of crazy  |
This is the team who’s brought us ADHD (Active Defense Harbinger Distribution and Recon-ng, both prior toolsmith topics. As such, I stalk their site, blog, and Twitter accounts like a tool nerd possessed, waiting for the next set of interesting bits to drop. RITA is very young in its development life cycle, not yet even two months from its initial release as this is written. That does not mean it should not be brought to your immediate attention. On 4 DEC the Black Hills Info Sec team updated RITA’s Bro logs import capabilities, her moment had arrived.
From RITA’s readme.md: “RITA is a toolkit which is intended to help approach the often overwhelming task of combing through piles of log data looking for suspect behavior.
RITA is intended to help in the search for indicators of compromise in enterprise networks of varying size. The framework was instructed by it’s engineers experience in penetration testing with the question of how they’d catch themselves, thus the analysis tends to looks specifically at the indicators their tools tend to leave behind.” This is the basis of a contemporary hunting practice, the definition of proper red team / blue team give and take. Emulate your adversary with the same tools they’d use (red), then write and implement detection and alerting logic to identify that same activity. You’ll force your red teams to become stealthier while improving your blue team tactics, all the while improving your likelihood of catching average and less sophisticated adversaries.
John and team have endeavored to document RITA, and while the docs are raw, they’ll definitely get you under way. Here’s a bit of a manifest to help bring you up to speed:
1) Initial video
2) Initial blog post
3) Release notes
4) Initial overview
5) Bro logs import overview
6) OVA for your preferred virtualization platform (works like a charm on VMWare)
Read all the docs, that’s an order, but I’ll give you my exact setup steps, which borrow liberally from the docs above…that you’re supposed to read.
1) Download and import the RITA OVA. Username: ht, password: !templinpw! (change it).
2) Crack open a terminal and run sudo apt-get update && sudo apt-get upgrade. Good time to take a VM snapshot.
3) Download bro_logs.tar.gz and logstash_script.tar.gz.
4) Create a logs directory, I used mkdir /home/ht/Documents/toolsmith.
5) Unpack bro_logs.tar.gz in your new directory, it created /home/ht/Documents/toolsmith/logs for me.
6) Unpack logstash_script.tar.gz in the new logs directory.
7) cd logstash_script.
8) chmod +x run.sh.
9) Edit bro.conf (line 128) such that imported Bro logs write to an index of your choosing. You’ll be shocked to learn that I chose toolsmith.
10) ./run.sh ../bro_meterpreter/2015-* ../dns_bro/2015-* ../powershell/2015-*
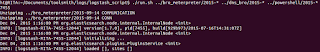 |
| Figure 1: Import in progress |
11) Browse to http://localhost:5601 to access Kibana. RITA runs on an ELK stack if you haven’t figured that out yet.
12) Go to Settings tab, change the index name to that which you selected above and add @timestamp under Time-field name resulting in something like Figure 2.
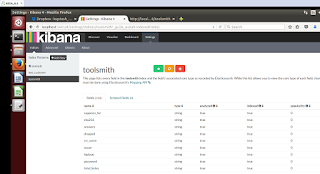 |
| Figure 2: Kibana Settings |
13) Go to Discover, and change time range from Last 15 Minutes to Last 5 Years. If all’s gone to plan you’ll see 572,687 entries.
14) Back at your terminal, cd Documents/RITA.
15) python run.py
16) Browse to http://localhost:5000 for the RITA UI
17) Enter the name of the index you created, should appear as in Figure 3
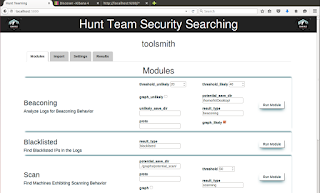 |
| Figure 3: RITA UI |
RITA gives you these capabilities in her current release:
Beaconing
Connections that happen frequently and on similar intervals could be an indicator of malware calling home
Blacklisted IPs
Blacklisted IPs are addresses reported as being involved with malware, spamming, and other dangerous activities
Scanning
These events occur when a computer attempts to connect to a large number of ports on a system, searching for vulnerabilities
Long Durations
Connections that are beyond the length of average on a network could indicate a compromised system
Long URLs
Longer than normal URLs could potentially be used to transfer malicious data into the system
Concurrent Logins
A user being logged into a high number of systems could indicate that this user’s account or original system has been compromised
Under Beaconing, change potential_save_dir to /home/ht/Desktop/ then click Run Module.
While you wait, you can watch progress in you terminal window.
| Figure 4: Beacon analysis progress |
Again, browse to http://localhost:5601, go to Discover, and change time range from Last 15 Minutes to Last 5 Years. You’ll see a slew of results for “unlikely beacons”; this will not do. We need likely beacons, or what’s the point? Search result_type:likely_beacons, and dig deeper. A number of the results seek destinations that are multicast addresses, let’s filter those out. I tried result_type:likely_beacons -239.255.255.250 and shrunk to load to three hits, two of which shared a destination IP of 107.170.48.146 as seen in Figure 5.
| Figure 5: Filtered beacons |
You should also see a number of PNG result files in /home/ht/Desktop by the way, which will visually help you confirm, Figure 5 does exactly that. Source IPs 192.168.56.72 and 192.168.0.23 are both communicating with 107.170.48.146 over HTTP.
| Figure 6: Beacons |
The beaconing is identified via a Fast Fourier Transform algorithm (FFT) generating graph that represents the results based on the time stamps for a given source/destination connection.
For continued pursuit of a culprit I then filtered with src:192.168.56.72 AND dst:107.170.48.146 -unlikely_beacons, which resulted in 49,611 hits.
Maybe an additional focus area from RITA’s list such as Long Durations? Yep, that worked. result_type=long_durations AND src=192.168.56.72 returned 60 hits including 54.192.89.85. That IP belongs to Amazon Web Services, nobody ever uses a cloud node for exfil or C2 during hacks or pentest work, right? 
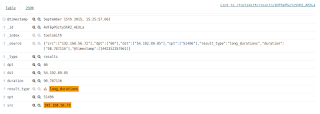 |
| Figure 7: Why is my IP having a long chat with an AWS node? |
Another interesting pivot may be to see what else your source IP has been up to at this point. I tried result_type=scanning AND src=192.168.56.72 and…what!…a scanning hit?
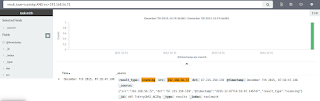 |
| Figure 8: Scanning |
You may notice that the dates are wonky, they represent when I ran the query rather that the date of the actual scanning activity. I re-queried just the destination IP, 67.215.250.139 in this case, and returned correct time stamps: September 16, 2015.
Sure, these are sample logs, but as an exercise opportunity, the work beautifully conveying how important it is to analyze from multiple perspectives.
Wrap Up
Yes, RITA is work in progress, but if you use it only as an excuse to improve you ELK stack fu, you’re already winning. Yes, we all love Splunk, but no we cannot all afford it. RITA and ELK go a long way down the path to free and open source alternatives, particularly for Bro users, which you should all be.
Keep an eye on this project, I love where it’s going, I’m betting the futures for this one.
Ping me via email or Twitter if you have questions: russ at holisticinfosec dot org or @holisticinfosec.
Cheers…until next month. Continue reading toolsmith #111: Lovely RITA, may I inquire?
We benefit this month from another offering first spotted via my fellow tool aficionados over at Toolswatch. And just like that, bam! A Beatles song…stuck in my head…all day.The crazy crew at Blackhills Security have embarked on another cool project: Real Intelligence Threat Analysis, or RITA, thus named because “Johns’ mom” was already taken.
 |
Yep, that kind of crazy  |
This is the team who’s brought us ADHD (Active Defense Harbinger Distribution and Recon-ng, both prior toolsmith topics. As such, I stalk their site, blog, and Twitter accounts like a tool nerd possessed, waiting for the next set of interesting bits to drop. RITA is very young in its development life cycle, not yet even two months from its initial release as this is written. That does not mean it should not be brought to your immediate attention. On 4 DEC the Black Hills Info Sec team updated RITA’s Bro logs import capabilities, her moment had arrived.
From RITA’s readme.md: “RITA is a toolkit which is intended to help approach the often overwhelming task of combing through piles of log data looking for suspect behavior.
RITA is intended to help in the search for indicators of compromise in enterprise networks of varying size. The framework was instructed by it’s engineers experience in penetration testing with the question of how they’d catch themselves, thus the analysis tends to looks specifically at the indicators their tools tend to leave behind.” This is the basis of a contemporary hunting practice, the definition of proper red team / blue team give and take. Emulate your adversary with the same tools they’d use (red), then write and implement detection and alerting logic to identify that same activity. You’ll force your red teams to become stealthier while improving your blue team tactics, all the while improving your likelihood of catching average and less sophisticated adversaries.
John and team have endeavored to document RITA, and while the docs are raw, they’ll definitely get you under way. Here’s a bit of a manifest to help bring you up to speed:
1) Initial video
2) Initial blog post
3) Release notes
4) Initial overview
5) Bro logs import overview
6) OVA for your preferred virtualization platform (works like a charm on VMWare)
Read all the docs, that’s an order, but I’ll give you my exact setup steps, which borrow liberally from the docs above…that you’re supposed to read.
1) Download and import the RITA OVA. Username: ht, password: !templinpw! (change it).
2) Crack open a terminal and run sudo apt-get update && sudo apt-get upgrade. Good time to take a VM snapshot.
3) Download bro_logs.tar.gz and logstash_script.tar.gz.
4) Create a logs directory, I used mkdir /home/ht/Documents/toolsmith.
5) Unpack bro_logs.tar.gz in your new directory, it created /home/ht/Documents/toolsmith/logs for me.
6) Unpack logstash_script.tar.gz in the new logs directory.
7) cd logstash_script.
8) chmod +x run.sh.
9) Edit bro.conf (line 128) such that imported Bro logs write to an index of your choosing. You’ll be shocked to learn that I chose toolsmith.
10) ./run.sh ../bro_meterpreter/2015-* ../dns_bro/2015-* ../powershell/2015-*
 |
| Figure 1: Import in progress |
11) Browse to http://localhost:5601 to access Kibana. RITA runs on an ELK stack if you haven’t figured that out yet.
12) Go to Settings tab, change the index name to that which you selected above and add @timestamp under Time-field name resulting in something like Figure 2.
 |
| Figure 2: Kibana Settings |
13) Go to Discover, and change time range from Last 15 Minutes to Last 5 Years. If all’s gone to plan you’ll see 572,687 entries.
14) Back at your terminal, cd Documents/RITA.
15) python run.py
16) Browse to http://localhost:5000 for the RITA UI
17) Enter the name of the index you created, should appear as in Figure 3
 |
| Figure 3: RITA UI |
RITA gives you these capabilities in her current release:
Beaconing
Connections that happen frequently and on similar intervals could be an indicator of malware calling home
Blacklisted IPs
Blacklisted IPs are addresses reported as being involved with malware, spamming, and other dangerous activities
Scanning
These events occur when a computer attempts to connect to a large number of ports on a system, searching for vulnerabilities
Long Durations
Connections that are beyond the length of average on a network could indicate a compromised system
Long URLs
Longer than normal URLs could potentially be used to transfer malicious data into the system
Concurrent Logins
A user being logged into a high number of systems could indicate that this user’s account or original system has been compromised
Under Beaconing, change potential_save_dir to /home/ht/Desktop/ then click Run Module.
While you wait, you can watch progress in you terminal window.
| Figure 4: Beacon analysis progress |
Again, browse to http://localhost:5601, go to Discover, and change time range from Last 15 Minutes to Last 5 Years. You’ll see a slew of results for “unlikely beacons”; this will not do. We need likely beacons, or what’s the point? Search result_type:likely_beacons, and dig deeper. A number of the results seek destinations that are multicast addresses, let’s filter those out. I tried result_type:likely_beacons -239.255.255.250 and shrunk to load to three hits, two of which shared a destination IP of 107.170.48.146 as seen in Figure 5.
| Figure 5: Filtered beacons |
You should also see a number of PNG result files in /home/ht/Desktop by the way, which will visually help you confirm, Figure 5 does exactly that. Source IPs 192.168.56.72 and 192.168.0.23 are both communicating with 107.170.48.146 over HTTP.
| Figure 6: Beacons |
The beaconing is identified via a Fast Fourier Transform algorithm (FFT) generating graph that represents the results based on the time stamps for a given source/destination connection.
For continued pursuit of a culprit I then filtered with src:192.168.56.72 AND dst:107.170.48.146 -unlikely_beacons, which resulted in 49,611 hits.
Maybe an additional focus area from RITA’s list such as Long Durations? Yep, that worked. result_type=long_durations AND src=192.168.56.72 returned 60 hits including 54.192.89.85. That IP belongs to Amazon Web Services, nobody ever uses a cloud node for exfil or C2 during hacks or pentest work, right? 
 |
| Figure 7: Why is my IP having a long chat with an AWS node? |
Another interesting pivot may be to see what else your source IP has been up to at this point. I tried result_type=scanning AND src=192.168.56.72 and…what!…a scanning hit?
 |
| Figure 8: Scanning |
You may notice that the dates are wonky, they represent when I ran the query rather that the date of the actual scanning activity. I re-queried just the destination IP, 67.215.250.139 in this case, and returned correct time stamps: September 16, 2015.
Sure, these are sample logs, but as an exercise opportunity, the work beautifully conveying how important it is to analyze from multiple perspectives.
Wrap Up
Yes, RITA is work in progress, but if you use it only as an excuse to improve you ELK stack fu, you’re already winning. Yes, we all love Splunk, but no we cannot all afford it. RITA and ELK go a long way down the path to free and open source alternatives, particularly for Bro users, which you should all be.
Keep an eye on this project, I love where it’s going, I’m betting the futures for this one.
Ping me via email or Twitter if you have questions: russ at holisticinfosec dot org or @holisticinfosec.
Cheers…until next month. Continue reading toolsmith #111: Lovely RITA, may I inquire?
| Figure 1 – Veil payload options |
| Figure 2 – Victim Meterpreter session |
| Figure 3 – Invoke-Mimikatz for the win! |

| Figure 4 – Rekall netstat plugin shows PowerShell with connections |
| Figure 5 – Rekall pstree plugin shows powershell.exe PPIDs |
 Note that the netstat plugin found that powershell.exe was connecting via 8443 (a “different” port number).
Note that the netstat plugin found that powershell.exe was connecting via 8443 (a “different” port number). | Figure 6 – Strings results for keyword search from memdump output |