How to Use CRM: A Beginners Guide
Learn how to use CRM with our introductory guide. Discover essential tips and a step-by-step tutorial to help you get started. Continue reading How to Use CRM: A Beginners Guide
Collaborate Disseminate
Learn how to use CRM with our introductory guide. Discover essential tips and a step-by-step tutorial to help you get started. Continue reading How to Use CRM: A Beginners Guide
Ransomware attacks have surged 78% year-over-year, affecting various sectors and organizations and significantly impacting supply chains. In this Help, Net Security video, Craig Birch, Technology Evangelist, and Principal Security Engineer at Cayosoft,… Continue reading Why ransomware attackers target Active Directory
In this Help Net Security interview, Jean-Philippe Aumasson, discusses the writing and research process for Serious Cryptography, his latest book. With a career steeped in research and practical cryptography, Aumasson offers a rare glimpse into the eff… Continue reading Behind the scenes of Serious Cryptography

[Marius Taciuc’s] latest endeavor, the B4 Thinker, offers a captivating glimpse into microcontroller architecture through a modular approach. This proof-of-concept project is meticulously documented, with a detailed, step-by-step guide to …read more Continue reading Building a Microcontroller from Scratch: The B4 Thinker Project
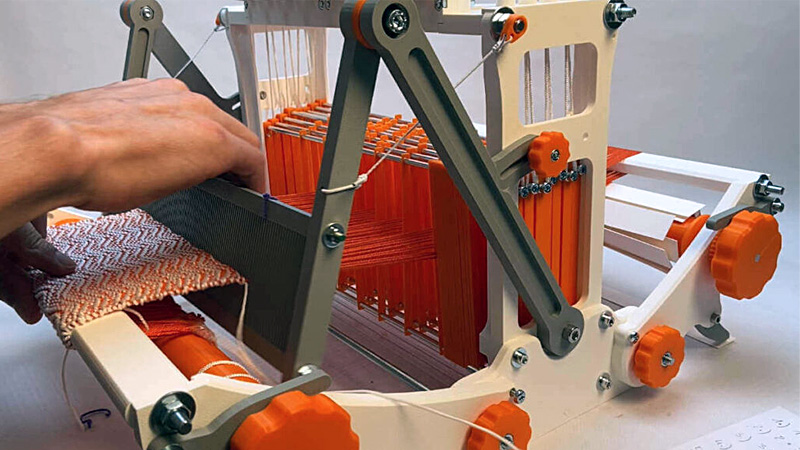
The loom has been a transformative invention throughout history, shaping the textile industry from simple hand looms to complex, fully automated machines. Now, thanks to advancements in 3D printing, this …read more Continue reading Simple 3D-Printed Table Loom for Complex Weavings
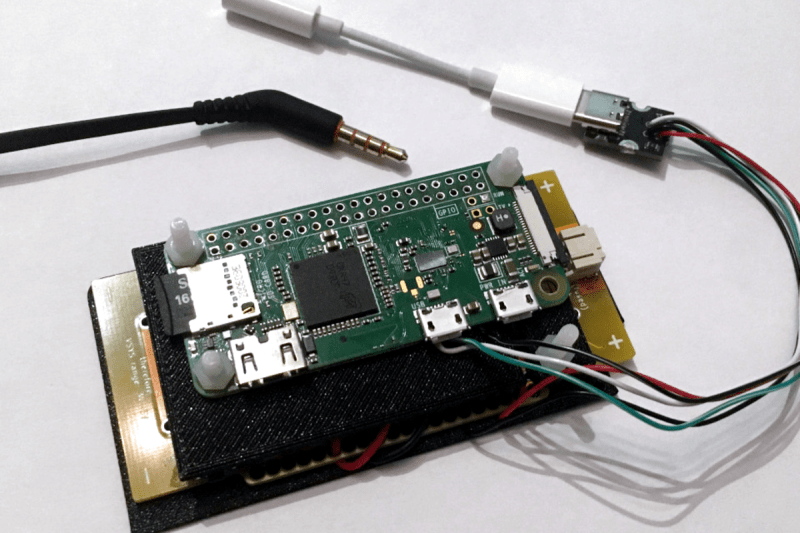
There are a ton of fun Raspberry Pi and Linux projects that require audio output – music players, talking robots, game consoles and arcades, intelligent assistants, mesh network walkie-talkies, and …read more Continue reading Audio On Pi: Here Are Your Options

Last time, I talked about how MicroPython is powerful and deserving of a place in your toolkit, and it made for a lively discussion. I’m glad to see that overall, …read more Continue reading Embedded Python: MicroPython Toolkits
As businesses strive to protect their data and privacy, the demand for skilled cybersecurity professionals continues to grow. This article provides expert advice to help you navigate the early stages of your cybersecurity career, offering practical tip… Continue reading How to start your cybersecurity career: Expert tips and guidance

An EDF (electric duct fan) is a motor that basically functions as a jet engine for RC aircraft. They’re built for speed, but to improve maneuverability (and because it’s super cool) …read more Continue reading Watch This RC Jet Thrust System Dance
In this Help Net Security video, Aaron Walton, Threat Intel Analyst at Expel, discusses travel scams. For the past 18 months, the Expel SOC team has observed a campaign targeting administrative credentials for Booking.com. The attackers create phishing… Continue reading Travel scams exposed: How to recognize and avoid them