Hacking an IoT Camera Reveals Hard-Coded Root Password
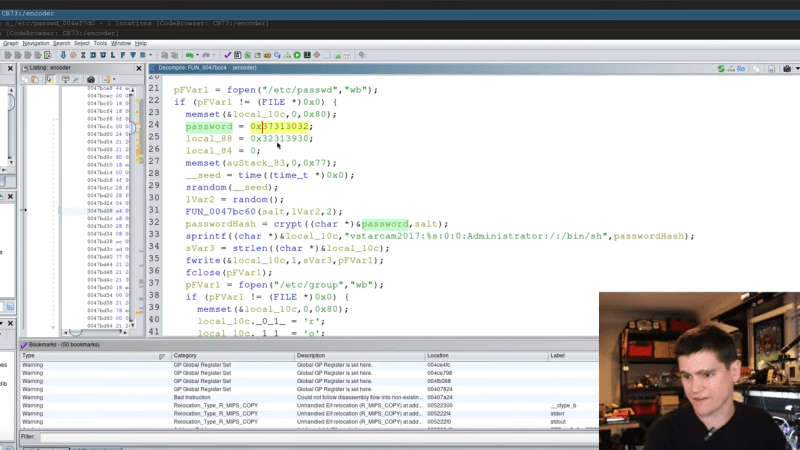
Hacking — at least the kind where you’re breaking into stuff — is very much a learn-by-doing skill. There’s simply no substitute for getting your hands dirty and just trying …read more Continue reading Hacking an IoT Camera Reveals Hard-Coded Root Password