Critical Stack provides a free threat intelligence aggregation feed through their
Intel Market for consumption by the
Bronetwork security monitoring platform. This is a fantastic service that is provided for free!! Special thanks to those who have contributed their feeds for all to take advantage of the benefits!! Installation is beyond the scope of this post as it is super easy with decent documentation available on their website. The feed updates run roughly hourly by default into a tab delimited file available on disk.
My goal was to make the IP address, domain and hash values accessible through a web interface for consumption by other tools in your security stack. Additionally, I didn’t want to create another database structure but be able to read the values into memory for comparison on script restarts. Decided to use Twisted Python by
Twisted Matrix Labs to create the web server. Twisted is an event-driven networking engine written in Python. The script provides a basic foundation without entering into the format debate between STIX and JSON.
Kept it simple…
Twisted Python Installation
The following installation steps work on Ubuntu 14.04 as that is my preference.
1. apt-get install build-essential python-setuptools python-dev python-pip
2. pip install service_identity
3. wget https://pypi.python.org/packages/source/T/Twisted/Twisted-15.5.0.tar.bz2
4. bzip2 -d Twisted-15.5.0.tar.bz2
5. tar -xvf Twisted-15.5.0.tar
6. cd Twisted-15.5.0/
7. python setup.py install
The PIP package installation allows for the future usage of SSL and SSH capabilities in Twisted.
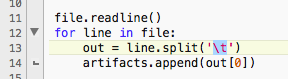
The default installation file and path containing the Critical Stack Intel Feed artifacts.
The field separator on each line that gets loaded into the Python list in memory.
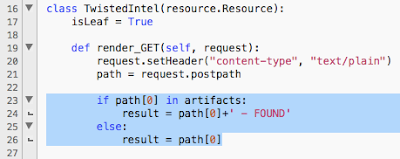
The output that gets displayed on the dynamically generated web page based on user input.
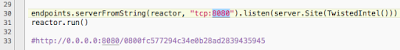
The port that the web server runs on for the end-user to access the web page.
The TwistedIntel.py script can be used after execution by browsing to the website with an IP address, domain or hash value provided in the path. If the result returns FOUND that means it is part of the Critical Stack Intel Feed as shown in Example 1. Example 2 depicts the results if the comparison does not find a matching value.
Example 1:
http://example.4n6ir.com:8080/www.evil.com
Result 1:
www.evil.com – FOUND
Example 2:
http://example.4n6ir.com:8080/www.good.com
Result 2:
www.good.com
Feel free to change the code to meet your needs and really appreciate any contributions back to the DFIR community.
Happy Coding!!
John Lukach
@FileBlocks
· TwistedIntel2.py displays the feed that an IP address, domain, or hash originated.
· Upstart configuration file for running the Twisted Python script at startup.
· Crontab configuration that restarts the script hourly after Critical Stack Intel updates.
Continue reading Critical Stack Intel Feed Consumption→