Tiny Bubbles in the Memory

We are always fascinated by bubble memory. In the late 1970s, this was the “Next Big Thing” that, as you may have guessed, was, in fact, not the next big …read more Continue reading Tiny Bubbles in the Memory
Collaborate Disseminate

We are always fascinated by bubble memory. In the late 1970s, this was the “Next Big Thing” that, as you may have guessed, was, in fact, not the next big …read more Continue reading Tiny Bubbles in the Memory
The Certification Authority/Browser Forum “is a cross-industry group that works together to develop minimum requirements for TLS certificates,” writes Google’s Security blog. And earlier this month two proposals from Google’s forward-looking roadmap “b… Continue reading HTTPS Certificate Industry Adopts New Security Requirements
Explore the top data governance tools of 2025 designed to enhance data security, compliance and management. Continue reading 7 Top Data Governance Tools in 2025
Organizations should not shy away from taking advantage of AI tools, but they need to find the right balance between maximizing efficiency and mitigating organizational risk. They need to put in place: 1. A seamless AI security policy AI may have previ… Continue reading Two things you need in place to successfully adopt AI
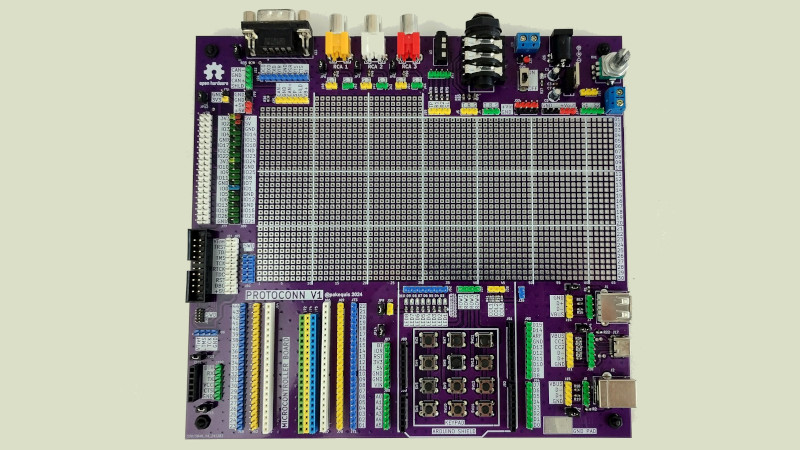
Prototyping is a personal affair, with approaches ranging from dead-bug parts on tinplate through stripboard and protoboard, to solderless breadboards and more. Whichever you prefer, a common problem is that …read more Continue reading A Prototyping Board With Every Connector
Exegol is a community-driven hacking environment, which helps users deploy hacking setups quickly and securely. It’s made for penetration testers, CTF players, bug bounty hunters, researchers, defenders, and both new and experienced users. Exegol… Continue reading Exegol: Open-source hacking environment
“The big set of open-source graphics driver updates for Linux 6.15 have been merged,” writes Phoronix, “but Linux creator Linus Torvalds isn’t particularly happy with the pull request.”
The new “hdrtest” code is for the Intel Xe kernel driver and is a… Continue reading Linus Torvalds Gently Criticizes Build-Slowing Testing Code Left in Linux 6.15-rc1
The large volume of security alerts, many created by automated tools, is overwhelming security and development teams, according to the 2025 Application Security Benchmark report by Ox Security. The report is based on an analysis of over 101 million app… Continue reading Only 2-5% of application security alerts require immediate action
The amount of data being shared by businesses with GenAI apps has exploded, increasing 30x in one year, according to Netskope. The average organization now shares more than 7.7GB of data with AI tools per month, a massive jump from just 250MB a year ag… Continue reading GenAI turning employees into unintentional insider threats
Deepfakes are a type of synthetic media created using AI and machine learning. In simple terms, they produce videos, images, audio, or text that look and sound real, even though the events depicted never actually happened. These altered clips spread ac… Continue reading How to recognize and prevent deepfake scams