CachyOS vs Nobara: Which is right for you?
Sometimes, a somewhat obscure Linux distribution might be just what you’re looking for. Is either CachyOS or Nobara the one? Continue reading CachyOS vs Nobara: Which is right for you?
Collaborate Disseminate
Sometimes, a somewhat obscure Linux distribution might be just what you’re looking for. Is either CachyOS or Nobara the one? Continue reading CachyOS vs Nobara: Which is right for you?
Upcoming software purchases should no longer be one-time contracts; they’re living partnerships built on shared data and trust. Continue reading The great software pricing shakeout of 2026: What every IT leader needs to know
Phones, smart glasses, and other camera-equipped devices capture scenes that include people who never agreed to be recorded. A newly published study examines what it would take for bystanders to signal their privacy choices directly to nearby cameras. … Continue reading What if your face could say “don’t record me”? Researchers think it’s possible
Kaspersky GReAT experts analyze the Evasive Panda APT’s infection chain, including shellcode encrypted with DPAPI and RC5, as well as the MgBot implant. Continue reading Evasive Panda APT poisons DNS requests to deliver MgBot
theodp writes: We all mix pictures, emojis, and text freely in our communications. So why not in our code? That’s the premise of “Fun With Python and Emoji: What Might Adding Pictures to Text Programming Languages Look Like?” (two-image Bluesky explain… Continue reading What Might Adding Emojis and Pictures To Text Programming Languages Look Like?
Conjur is an open-source secrets management project designed for environments built around containers, automation, and dynamic infrastructure. It focuses on controlling access to credentials such as database passwords, API keys, and tokens that applica… Continue reading Conjur: Open-source secrets management and application identity
AI security has reached a point where enthusiasm alone no longer carries organizations forward. New Cloud Security Alliance research shows that governance has become the main factor separating teams that feel prepared from those that do not. Governance… Continue reading Governance maturity defines enterprise AI confidence
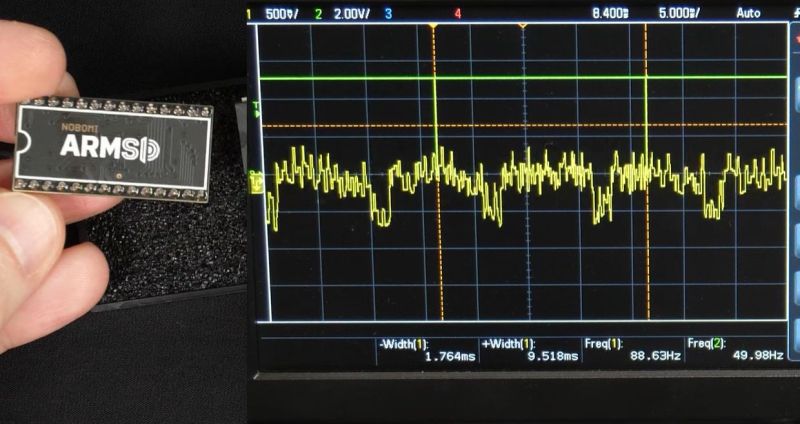
Despite the Commodore 64 having been out of production for probably longer than many Hackaday readers have been alive, its SID audio chip remains a very popular subject of both …read more Continue reading Exploring Modern SID Chip Substitutes
Elementary OS 8.1 is now available for download and shipping on select hardware from retailers such as Star Labs, Slimbook, and Laptop with Linux. The update arrives after more than a year of refinements based on community feedback and issue reports. T… Continue reading Elementary OS 8.1 rolls out with a stronger focus on system security
Counterfeit protection often leans on the idea that physical materials have quirks no attacker can copy. A new study challenges that comfort by showing how systems built on paper surface fingerprints can be disrupted or bypassed. The research comes fro… Continue reading Counterfeit defenses built on paper have blind spots