Do you know what is on your network? Do you have a record of truth like DHCP logs for connected devices? How do you monitor for unauthorized devices? What happens if none of this information is currently available?
Nathan Crews @crewsnw1 and Tanner Payne @payneman at the Security Onion Conference 2016 presented on Simplifying Home Security with CHIVE that will definitely help those with Security Onion deployed answer these questions. Well worth the watch: https://youtu.be/zBDAjNnRiQI
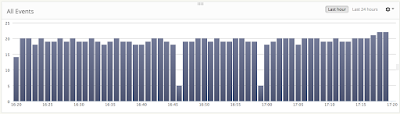
My objective is to create a Python script that helps with the identification of devices on the network using Nmap with limited configuration. I want to be able to drop a virtual machine or Raspberry Pi onto a network segment that will perform the discovery scans every minute using a cron job. Generating output that can be easily consumed by a SIEM for monitoring.
I use the netifaces package to determine the network address that was assigned to the device for the discovery scans.
I use the netaddr package to generate the network cidr format that the Nmap syntax uses for scanning subnet ranges.
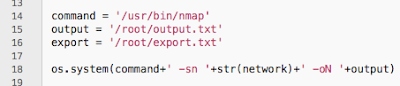
The script will be executed from cron thus running as the root account, so important to provide absolute paths. Nmap also needs permission to listen to network responses that is possible at this permission level too.
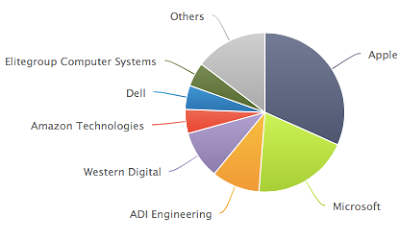
I take the multi-line native Nmap output and consolidate it down to single lines. The derived fields are defined by equals (=) for the labels and pipes (|) to separate the values. I parse out the scan start date, scanner IP address, identified device IP address, identified device MAC address and the vendor associated with the MAC address.
I ship the export.txt file to Loggly (https://www.loggly.com) for parsing and alerting as that allows me to focus on the analysis not the administration.
The full script can be found on GitHub: https://gist.github.com/jblukach/c67c8695033ad276b4836bea58669958
John Lukach
@jblukach
@jblukach