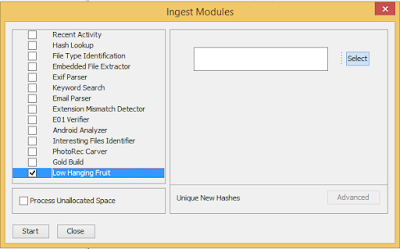
I wanted to try out the second Python module tutorial from Basis Technology [1]. After completing hash analysis to identify known files from the NSRL, the remaining hashes can be checked for low hanging fruit a.k.a. potential bugs. The module will export a unique list of hashes not marked as known into the case folder as a file called AllLowHangingFruit.txt that can be run against Virus Total or Team Cymru [2][3].
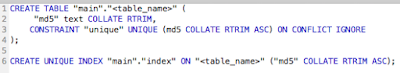
Running the same hashes over and over is not always a good use of resources thus added a GUI that would allow the end-user to select a SQLite database storing a list of previously seen hashes [4]. An empty SQLite database is posted on GitHub with the module code or you can always create your own too.
If the location of the SQLite file is selected than the module checks to see if the hash is marked as known or in the database prior to exporting the value. It is left to your discretion whether to manually add the hashes to the database for exclusion in the future from the NewLowHangingFruit.txt file.
Links