The 8 Best Network Monitoring Tools for 2024
The best network monitoring tools include Zabbix, Datadog, and Cacti. Compare features, pricing, and supported platforms among our top picks. Continue reading The 8 Best Network Monitoring Tools for 2024
Collaborate Disseminate
The best network monitoring tools include Zabbix, Datadog, and Cacti. Compare features, pricing, and supported platforms among our top picks. Continue reading The 8 Best Network Monitoring Tools for 2024
I know that port scanning can set off IDS systems on certain networks due to the suspicious traffic it generates. Can the usage of Wireshark be detected on a network? If so, will using it set off any alert systems, and can it be traced bac… Continue reading Can the usage of Wireshark be detected when sniffing for packets in promiscuous mode? [duplicate]
I am able to search for a string in the in packet bytes of a pcap capture using Wireshark. Is there similar functionality available in tshark ?
I already have the pcap files. But I need to go through them quickly to find the matching strin… Continue reading Search for a string in packet bytes of a pcap file using tshark [migrated]
I am looking for a technique to capture the full TLS request coming from a UWP application that I do not manage, but I do have full access to the client (aka my personal computer).
Through Wireshark, I’ve confirmed that the application is … Continue reading Capturing and decrypting TLS content on local machine
I’m running a pentest and I’ve managed to get man-in-the-middle access between a machine and a domain controller. A process on the machine will log into the DC, as a domain admin, to get a Kerberos ticket. I can see the AS-REQ/AS-REP &… Continue reading How to extract Kerberos ticket from Wireshark?
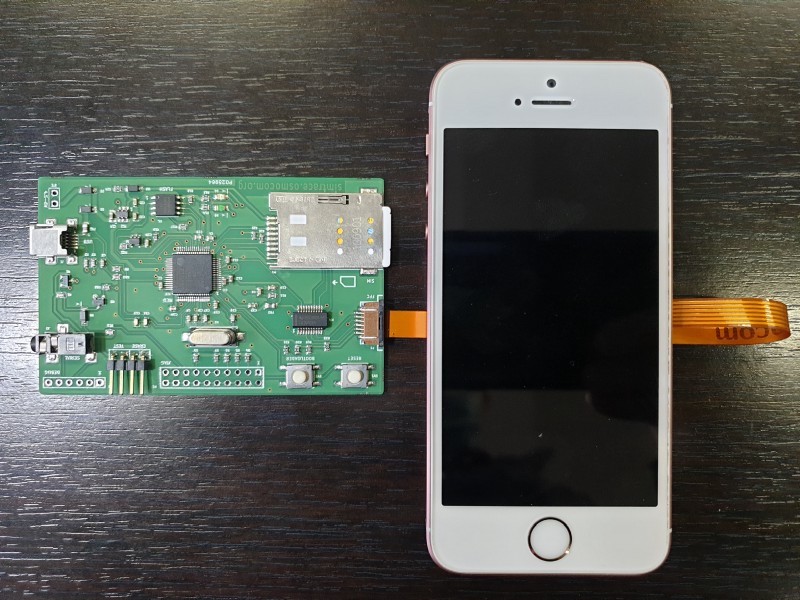
The modern smartphone is a marvel of sensors, radios, inputs, outputs, and processing power. In particular, some of those radios, such as WiFi and cellular, have grown fiendishly complex over …read more Continue reading Diving the Depths of Ma Bell
I have my domain .key and .crt file.
the key file include "—–BEGIN PRIVATE KEY—–"
when i use command on centos:
tshark -r /tmp/xx.pcap -o ‘ssl.keys_list:any,443,http,/tmp/private.key’ -o ‘ssl.debug_file:/tmp/ssl.log’ -Y htt… Continue reading How to decrypt HTTPS traffic with tshark when I have the .key and .crt file?
I’ve recently decrypted my TLS traffic from Chrome to better inspect my PC’s network behaviour.
PRTG Monitor on my PC seems to be sending a GET request for the login page assigned to the router’s gateway address. Not necessarily proof it’s… Continue reading PC sending GET requests to router page by itself? [closed]
Originally posted on Network Engineering:
To Summarize, the total of my subprotocol/subvariant packet percentages do not sum up to its header, the total TCP % Packets noted by the tool. Transport Layer Protocols may not need to add up in… Continue reading Wireshark -Protocol Hierarchy Omitting large amount of subprotocol traffic [closed]
When sniffing network traffic, one can see an HTTPS packet and all its (encrypted) data.
I am wondering what would happen if this packet is copied and then re-sent.
Is there a protocol at some layer that prevents the same packet being used… Continue reading Can an HTTPS request be sent twice?