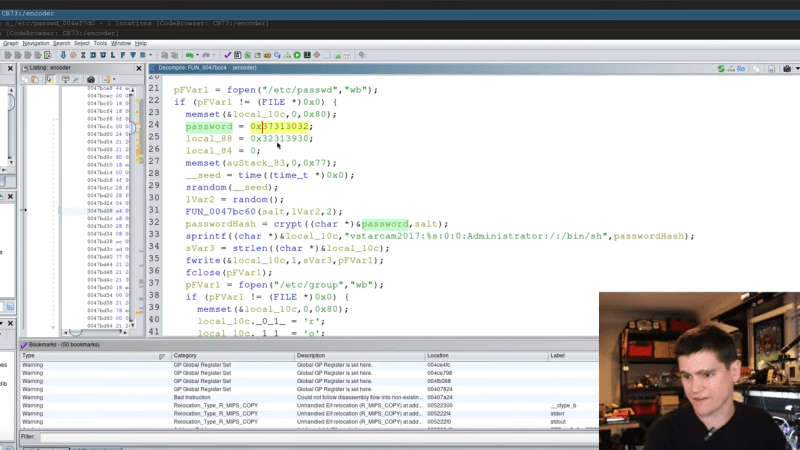
Root takeover attack on Kubernetes host despite Vault agent
HashiCorp Vault Agent creates a sidecar that talks to the Vault server and injects secrets as files into containers, where the files are located under /vault/secrets/.
"render all defined templates to the ephemeral in-memory mount at … Continue reading Root takeover attack on Kubernetes host despite Vault agent