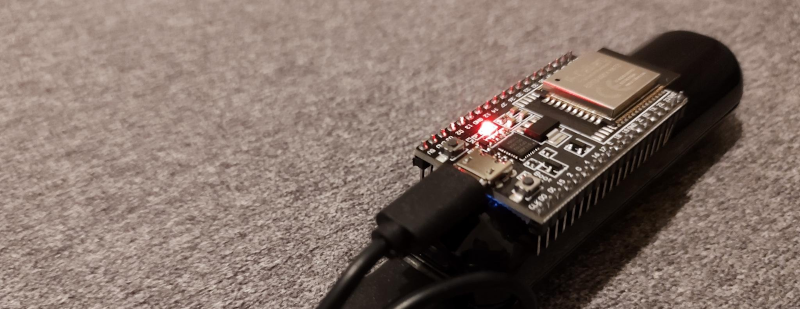
Check Your Mailbox Using The AirTag Infrastructure

When a company creates an infrastructure of devices, we sometimes subvert this infrastructure and use it to solve tricky problems. For example, here’s a question that many a hacker has …read more Continue reading Check Your Mailbox Using The AirTag Infrastructure