Linux Fu: Failing Pipelines

Bash is great for automating little tasks, but sometimes a little script you think will take a minute to write turns into a half hour or more. This is the …read more Continue reading Linux Fu: Failing Pipelines
Collaborate Disseminate

Bash is great for automating little tasks, but sometimes a little script you think will take a minute to write turns into a half hour or more. This is the …read more Continue reading Linux Fu: Failing Pipelines
Someone know how is leaking virtual card numbers?
I have few, but only leaking is for online payments.
Not used is frozen.
That is systematic.
I have a lot extension in Firefox for protection [only safety sources].
On tablet with Android f… Continue reading Leaking virtual card numbers – systemically [closed]
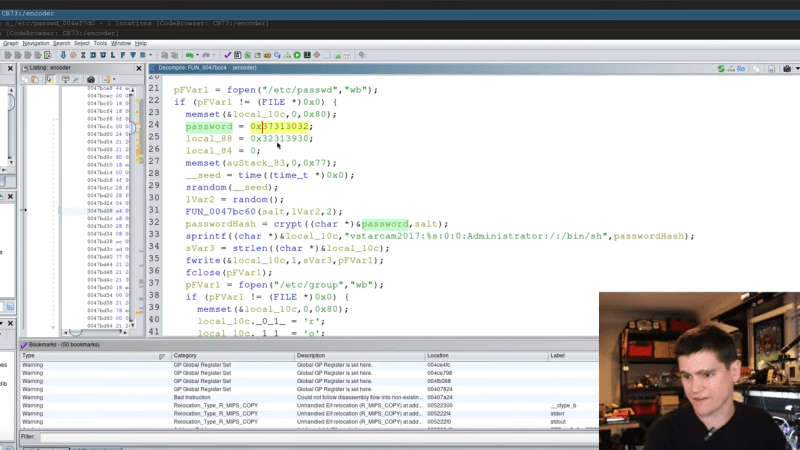
Hacking — at least the kind where you’re breaking into stuff — is very much a learn-by-doing skill. There’s simply no substitute for getting your hands dirty and just trying …read more Continue reading Hacking an IoT Camera Reveals Hard-Coded Root Password
I’m working on a TryHackMe problem (Task 15 here) to exploit a vulnerable component of a website to gain RCE and then read the contents of /opt/flag.txt.
The targeted website uses an IP generated by TryHackMe which is different on each att… Continue reading Why can I cat a file I can’t find?
Linux kernel has a feature to verify Linux kernel modules before loading them. This verification assures that modification made to Linux kernel is authentic. Does kernel have similar features to validate each application/binary while launc… Continue reading Verify Executables/Application before launching [duplicate]
Play Ransomware Targets Linux! New Variant Attacks ESXi with Prolific Puma Ties. Learn how to protect your organization… Continue reading Play Ransomware Variant Targeting Linux ESXi Environments
I was trying to overflow the return pointer of a simple program. I have asrl disabled and I compiled like this gcc returnexp.c -o returnexp -fno-stack-protector.
(I would disable noexecstack later on when I could overwrite the pointer)
Bu… Continue reading Segmentation fault without rip even getting overwritten Buffer Overflow
I’ve the following nftable configuration (/etc/nftables.conf) to enforce a "VPN kill switch". Except for ICMP and IGMP, connections are only allowed through tun0. This works well as a "kill switch".
#!/usr/sbin/nft -f
… Continue reading How can there be incoming connections when using a VPN?
According to this RedHat knowledge base entry CrowdSource has similarly caused a kernel panic on Linux as well with eBPF program.
My question is how is this possible? eBPF is described as,
eBPF changes this formula fundamentally. It allow… Continue reading How does an eBPF program cause a kernel panic?
We start sshd using xinetd on our gateway. Here is the xinetd config file:
service ssh
{
instances = 10
socket_type = stream
wait = no
user = root
protocol = tcp
server … Continue reading sshd won’t start from xinetd in OpenSSH 9.8p1 [migrated]