Working with BGAs: Soldering, Reballing, and Rework
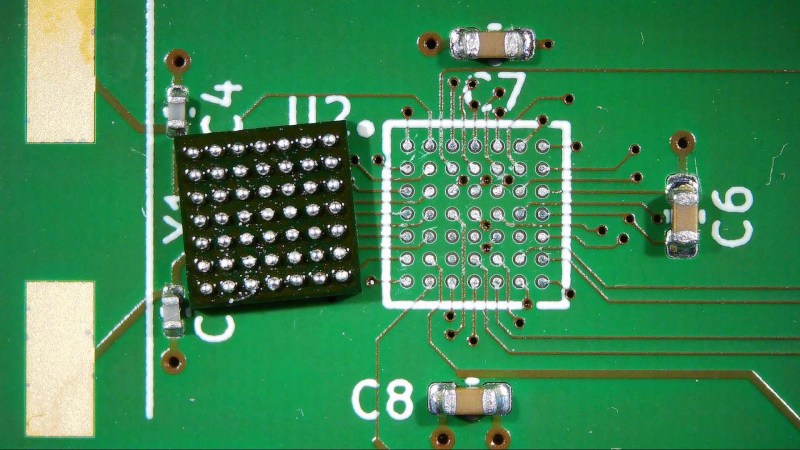
In our previous article on Ball Grid Arrays (BGAs), we explored how to design circuit boards and how to route the signals coming out of a BGA package. But designing …read more Continue reading Working with BGAs: Soldering, Reballing, and Rework