Need To Dump A Protected STM32F0x? Use Your Pico!
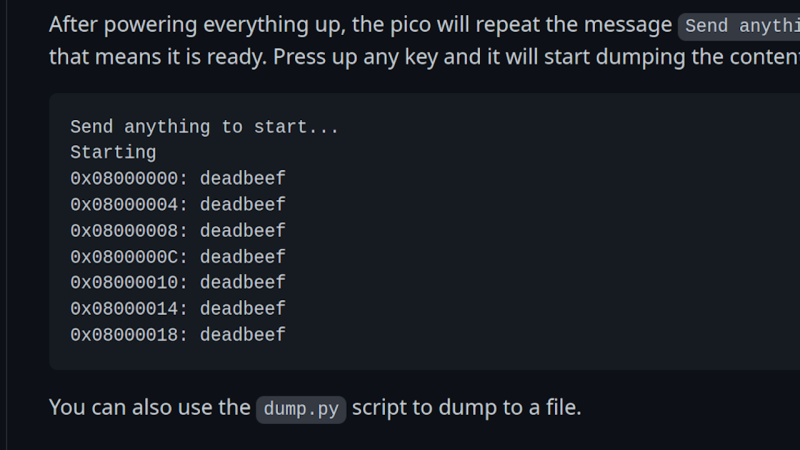
Sometimes, security mechanisms can be bypassed if you just do things slightly out of the ordinary. For instance, readout protection on microcontrollers is a given nowadays, to the point where …read more Continue reading Need To Dump A Protected STM32F0x? Use Your Pico!