Detect Starlink Satellites Passing By
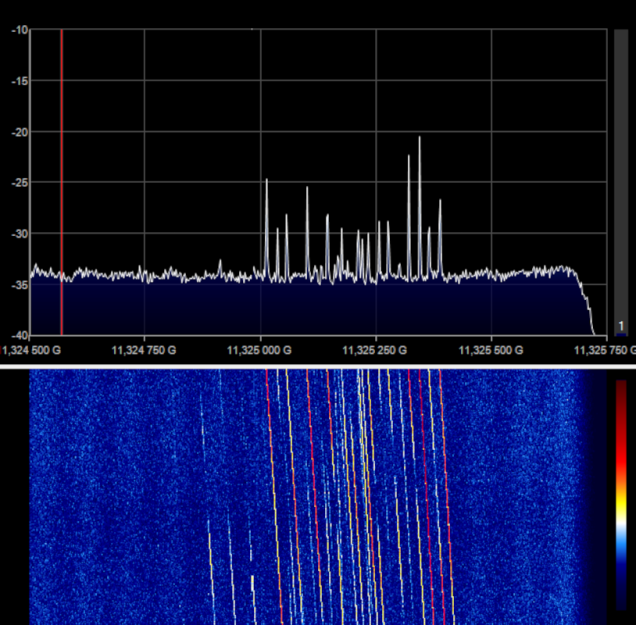
The Starlink beta has semi-officially ended, but it seems as though the global chip shortage is still limiting how many satellites are flying around the world for broadband internet access …read more Continue reading Detect Starlink Satellites Passing By
