Homebrew CPU Gets a Beautiful Rotating Cube Demo
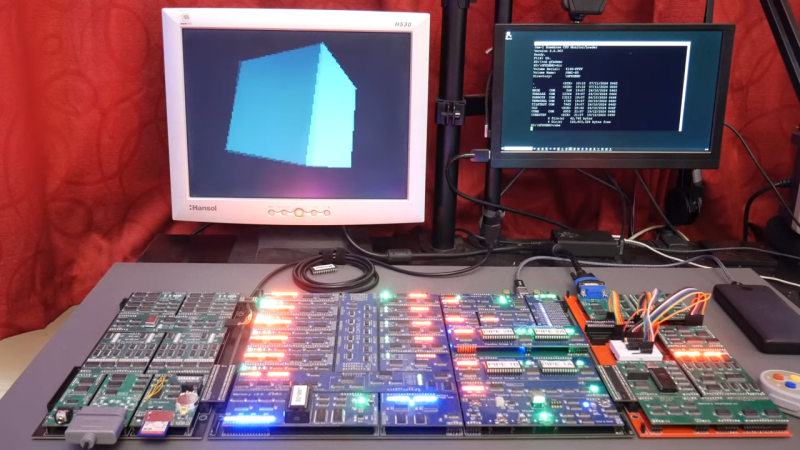
[James Sharman] designed and built his own 8-bit computer from scratch using TTL logic chips, including a VGA adapter, and you can watch it run a glorious rotating cube demo …read more Continue reading Homebrew CPU Gets a Beautiful Rotating Cube Demo