The Pros and Cons of Bitcoin
Bitcoin, the first and most popular cryptocurrency, offers high potential returns but comes with high volatility and a… Continue reading The Pros and Cons of Bitcoin
Collaborate Disseminate
Bitcoin, the first and most popular cryptocurrency, offers high potential returns but comes with high volatility and a… Continue reading The Pros and Cons of Bitcoin
I apologise in advance if this is a dumb question. But this seems like one of those straight forward things that are so straight forward that its not even mentioned and I am not getting it.
Perhaps I am too used to the simplistic client / … Continue reading How does JWE secure the Content Encryption Key
This isn’t good:
On Thursday, researchers from security firm Binarly revealed that Secure Boot is completely compromised on more than 200 device models sold by Acer, Dell, Gigabyte, Intel, and Supermicro. The cause: a cryptographic key underpinning Secure Boot on those models that was compromised in 2022. In a public GitHub repository committed in December of that year, someone working for multiple US-based device manufacturers published what’s known as a platform key, the cryptographic key that forms the root-of-trust anchor between the hardware device and the firmware that runs on it. The repository was located at https://github.com/raywu-aaeon/Ryzen2000_4000.git, and it’s not clear when it was taken down…
As part of TLS1.3 handshake client hello sent containing the TLS1.3 version support as part of suppored_versions extension, consider if as part of server hello supported_versions extension is not present, but Legacy_version is set to 0x030… Continue reading In TLS1.3 server hello can the legacy version field set to 0x0304
The question is not about generating pseudo-random numbers with linear congruential generator.
A linear congruential generator (LCG) is defined by the recurrence relation:
[ X_{n+1} = (a X_n + c) \mod m ]
Can LCG be used in public-key cryp… Continue reading Can linear congruential generator be used in public-key cryptography? [closed]
I’ve read the article from Unciphered about it, multiple times, and still fail to understand it.
It basically says that wallets generated by the BitcoinJS front-end library from 2011 to 2015 are vulnerable because of poor randomness genera… Continue reading What exactly is the Randstorm vulnerability?
"The KeyUpdate handshake message is used to indicate that the sender is updating its sending cryptographic keys."
"If the request_update field is set to "update_requested", then the receiver MUST send a KeyUpdate o… Continue reading what should be the response of keyupdate if the initial KeyUpdateRequest is set to update_not_requested not update_requested
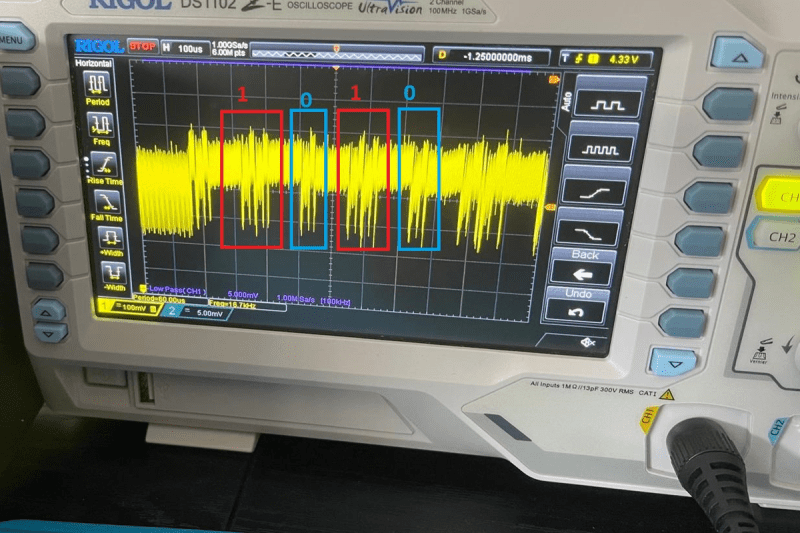
Cryptography ain’t easy. Seemingly small details like how many times a computationally intensive loop runs can give the game away. [Lord Feistel] gives us a demo of how this could …read more Continue reading Undo Arduino Encryption with an Oscilloscope
Password-authenticated key exchange (PAKE) is a method in which two or more parties, based on their knowledge of a shared password,
establish a cryptographic key using an exchange of messages, such that
an unauthorized party (one who cont… Continue reading benefits of a common session key over a common password
Password-authenticated key exchange (PAKE) is a method in which two or more parties, based on their knowledge of a shared password,
establish a cryptographic key using an exchange of messages, such that
an unauthorized party (one who cont… Continue reading benefits of a common session key over a common password