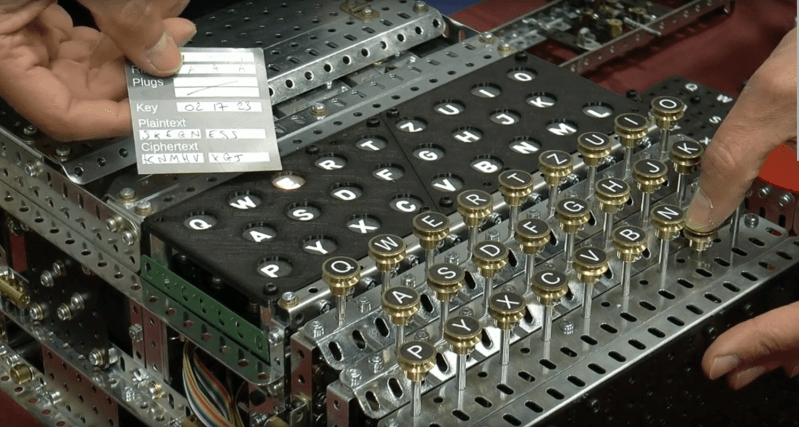
EPROM-based Enigma Machine
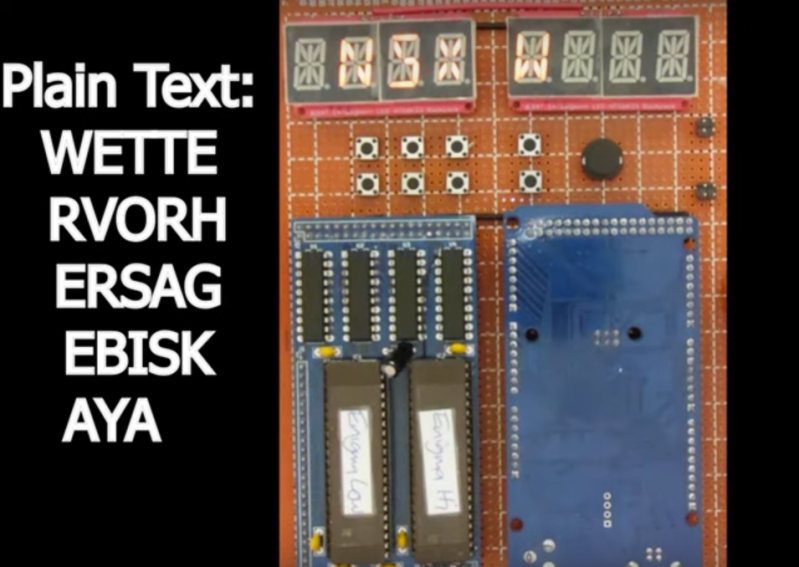
The Enigma machine is perhaps one of the most legendary devices to come out of World War II. The Germans used the ingenious cryptographic device to hide their communications from …read more Continue reading EPROM-based Enigma Machine