Linux Fu: A Warp Speed Prompt

If you spend a lot of time at the command line, you probably have either a very basic prompt or a complex, information-dense prompt. If you are in the former …read more Continue reading Linux Fu: A Warp Speed Prompt
Collaborate Disseminate

If you spend a lot of time at the command line, you probably have either a very basic prompt or a complex, information-dense prompt. If you are in the former …read more Continue reading Linux Fu: A Warp Speed Prompt

You can argue if bash is a good programming language or not, but you can’t argue that it is a programming language. However, there are a few oddities about it …read more Continue reading Linux Fu: Use the Source (Command), Luke

Wolfenstein 3D was a paradigm-shifting piece of software, using raycasting techniques to create a game with pseudo-3D graphics. Now, [izabera] has done something very similar, creating a raycasting display engine that …read more Continue reading Building a Raycaster Within Bash

Are you familiar with huffman encoding? That’s where you pick shorter codes for more frequent letters. Morse code is the same way. Shorter characters are the ones you are most …read more Continue reading Optimizing Your Linux Shell Experience

By default, bash is the most popular command language simply because it’s included in most *nix operating systems. Additionally, people don’t tend to spend a lot of time thinking about …read more Continue reading Alternatives Don’t Need to be Bashed
If $1 contains untrusted user input for example $(whoami). Are any of the following bash examples vulnerable to command injection?
I’m having issues clearly understanding this behavior in Bash. Also, I have issues with echo -n "$1&quo… Continue reading Are these bash lines (handling untrusted user input) vulnerable to command injection?
tldr: is using a script spawned by my main process, which reads only a chunk of a sensitive file then passing the result to my main process – of any benefit?
in contrast to loading the file in my main process?
background:
I’m building my … Continue reading benefit to reading sensitive file chunks via a "middleman" shell script?
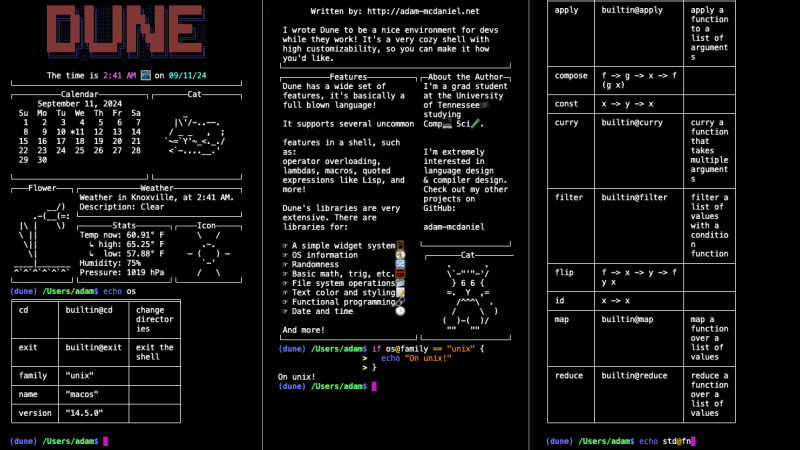
Lisp is one of those programming languages that seems to keep taunting us for not learning it properly. It is still used for teaching functional languages today. [Adam McDaniel] has …read more Continue reading Get Your Lisp On With The Dune Shell
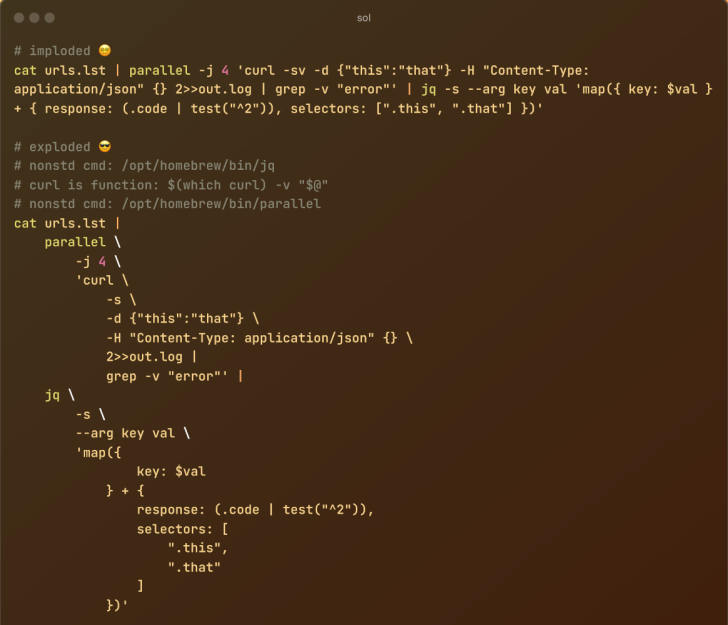
One of the most universal experiences of any Linux or Unix user is working through a guide or handbook and coming across an almost unbelievably complex line of code meant …read more Continue reading Blowing Up Shell Scripts
I’m reviewing code which apparently ignores all security standards but doesn’t seem to be exploitable due to its peculiar construction. The first stage is a Java Spring application and the name parameter is fully user-controlled.
String cm… Continue reading Is this code vulnerable to injection?