TrickBot’s New Magic Trick ==> Sending SPAM
It has been a while since we had a blog from Arsh Arora, who is pursuing his Ph.D., which has kept him away from blogging for a bit. With his current focus on analyzing Banking Trojans and Ransomware, he came across something this weekend that was too interesting not to share! Take it away, Arsh!
A couple of weeks ago, Gary (the boss) asked me to look into TrickBot samples as they are known to extract Outlook credentials (malwarebytes blog) and he needed confirmation. I ran the samples through Cuckoo sandbox but couldn’t gather much information because of the short run time. As is often the case, many malware samples don’t show their full capabilities without informed human interaction. Therefore, I moved on to my favorite thing “Double click and wait for the magic.”
First Stage – Extracting the Config File
During the first run, Clifford Wilson, a new malware researcher in our lab, helped in extracting some valuable indicators. In the initial stage, we found out that when testing the TrickBot binary:
Original binary hash – 0c9b1b5ce3731bf8dbfe10432b1f0c2ff48d3ccdad6a28a6783d109b1bc07183
Downloaded binary hash – ce806899fc6ef39a6f9f256g4dg3d568e46696c8306ef8ge96f348g9a68g6660
The original binary launches a child process and then it gets replaced by a different binary that is downloaded. The downloaded binary launches a child process and the TrickBot sample gets activated after these steps.
When analyzing we found out that it launches several “svchost.exe,” it varies from 4 to 7 depending upon the time of your run.
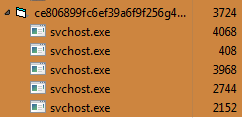 |
| Fig. 1: TrickBot binary with “svchost.exe” |
Each of the scvhost instances have their own significance:
Svchost 1: Appears to be used to search and receive certificates
Svchost 2: Contains strings referring to 127 different financial institutions. (complete list is mentioned below)
Svchost 3: Is the one that collects data from Outlook\Profiles such as username, password, servers, ports
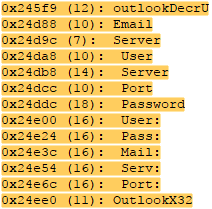 |
| Fig. 2: Outlook exfiltration |
Svchost 4: Scans the internet history to search for stored credentials
Svchost 5: Contain a list of random email ids, research is being to understand the use of those emails.
Confirmation of Svchost being launched by TrickBot binary
In order to confirm our hypothesis about the various svchost being launched by a single process and not more than one processes, researchers tested a different binary and found the results to be identical. We used Process Monitor to confirm the creation of “Svchost.exe” by the same process.
 |
| Fig. 3: Svchost Create Process |
Config File : Svchost 2
adelaidebank[.]com[.]au
anzdirect[.]co[.]nz
anztransactive[.]anz[.]com
arabbank[.]com[.]au
asb[.]co[.]nz
bankcoop[.]ch
bankleumi[.]co[.]uk
bankline[.]natwest[.]com
bankline[.]rbs[.]com
bankofireland[.]com
bankofmelbourne[.]com[.]au
bankofscotland[.]co[.]uk
banksa[.]com[.]au
banksyd[.]com[.]au
bankwest[.]com[.]au
barclays[.]co[.]uk
barclays[.]com
barclayswealth[.]com
bcv[.]ch
bendigobank[.]com[.]au
beyondbank[.]com[.]au
bibplus[.]uobgroup[.]com
bizchannel[.]cimb[.]com
bmo[.]com
bmoharris[.]com
bnz[.]co[.]nz
boi-bol[.]com
boqspecialist[.]com[.]au
business[.]hsbc[.]co
cams[.]scotiabank[.]com
cibc[.]com
citibank[.]com[.]sg
citibusiness[.]citibank[.]com
coinbase[.]com
co-operativebank[.]co[.]uk
corp[.]westpac[.]co
corp[.]westpac[.]com
corpnet[.]lu
coutts[.]com
cua[.]com[.]au
danskebank[.]ie
defencebank[.]com[.]au
dev[.]bmo[.]com
ebanking[.]hsbc[.]co
ebanking[.]zugerkb[.]ch
fidunet[.]lu
flexipurchase[.]com
greater[.]com[.]au
gtb[.]unicredit[.]eu
harrisbank[.]com
heartland[.]co[.]nz
hsbc[.]com[.]au
humebank[.]com[.]au
hypovereinsbank[.]de
ib[.]boq[.]com
ib[.]kiwibank[.]co
icicibank[.]com
imb[.]com[.]au
internationalmoneytransfers[.]com[.]au
iombankibanking[.]com
kbc[.]ie
lloydsbank[.]co[.]uk
lloydsbank[.]com
lukb[.]ch
macquarie[.]com[.]au
maybank[.]com[.]sg
mebank[.]com[.]au
metrobankonline[.]co[.]uk
my[.]commbiz[.]commbank[.]au
mystate[.]com[.]au
nab[.]com[.]au
nationwide[.]co[.]uk
navyfederal[.]org
netteller[.]com[.]
newcastlepermanent[.]com[.]au
nwolb[.]com
ocbc[.]com
online[.]anz[.]com
online[.]lloydsbank[.]com
onlinebanking[.]iombank[.]com
onlinesbiglobal[.]com
postfinance[.]ch
qtmb[.]com[.]au
rabobank[.]co[.]nz
rabobank[.]com[.]au
rabodirect[.]co[.]nz
rabodirect[.]com[.]au
raiffeisendirect[.]ch
rbc[.]com
rbsdigital[.]com
rbsiibanking[.]com
ruralbank[.]com[.]au
salesforce[.]com
santander[.]co[.]uk
sbisyd[.]com[.]au
sbs[.]net[.]nz
scotiabank[.]com
secure[.]societegenerale[.]fr
secure[.]wellsfargo[.]com
standardchartered[.]com
standardchartered[.]com[.]sg
stgeorge[.]com[.]au
suncorpbank[.]com[.]au
tdcommercialbanking[.]com
tmbank[.]com[.]au
tsb[.]co[.]uk
tsbbank[.]co[.]nz
tsw[.]com[.]au
ubank[.]com[.]au
ubs[.]com
ulsterbankanytimebanking[.]co[.]uk
ulsterbankanytimebanking[.]ie
unicredit[.]it
unicreditbank[.]ba
unicreditbank[.]lu
unicreditbank[.]sk
unicreditbanking[.]net
unicreditcorporate[.]it
uobgroup[.]com
valiant[.]ch
wellsfargo[.]com
westpac[.]co[.]nz
westpac[.]com[.]au
This is the comprehensive list of all the unique financial institutions mentioned in the Svchost 2. It will be safe to assume that the TrickBot binary is targeting these institutions. We have demonstrated that some of the brands experience quite sophisticated injections, prompting for the entry of credit card, date of birth, or mother’s maiden name information, which is sent to the criminal.
The binary creates a folder ‘winapp’ under Roaming and stores all the files in that location, which is covered in the MalwareBytes blog. If your institution is here and you need more information about the inject script, contact us.
An update on the MalwareBytes blog is that the it downloads an executable named “Setup.exe” under WinApp. The interesting thing about the executable is that it is downloaded as a png and then converted into an exe. The URLs the executable is downloaded are:
http://www[.]aharonwheelsbolsta[.]com/worming[.]png
http://www[.]aharonwheelsbolsta[.]com/toler[.]png
 |
Fig. 4: File being downloaded as Png
 |
| Fig. 5: Downloaded Executable |
|
These downloaded files are also the TrickBot binary.
 |
| Fig. 6: Setup.exe under WinApp |
The downloaded files being converted into “Setup.exe” and can be found under the Roaming/WinApp directory.
Second Stage – Spam aka ‘Pill Spam’
After the completion of initial analysis, there was a strange pattern observed when analyzed the Wireshark traffic with ‘IMF’ filter. Our network (10.0.2.15) was used as a server along with being a proxy. Our address was proxy for other messages coming from 208.84.244.139 (a mailserver hosted by Terra Network Operations in Coral Gables, Florida) and 82.208.6.144 (a mailserver in Prague, Czech Republic.) Also, our network was sending outbound spam.
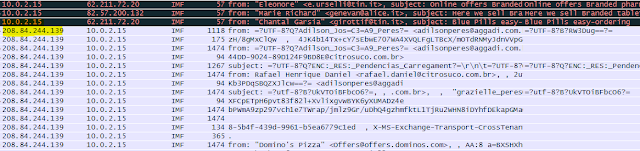 |
| Fig. 7: Wireshark capture with IMF filter |
Outbound Spam
As can be seen in the figure 7, top 3 spam messages are outbound and are being sent from our network. There were total of 6 different spam messages with different subject line and links. The email is mentioned below:
 |
| Fig. 8: Email message |
Following were some of the subjects and urls that were spammed.
Subject URL
| Affordable-priced Brand Pilules |
http://martinagebhardt[.]hu/w/1gox[.]php |
| Blue Pills easy-ordering |
http://host[.]teignmouthfolk[.]co[.]uk/w/zxaj[.]php |
| Eromedications Wholesale |
http://martinagebhardt[.]hu/w/1pyo[.]php |
| Great offers on Male Pills |
http://host.bhannu[.]com/w/w10x[.]php |
| Here we sell Branded tablets |
http://host[.]selfcateringintenerife[.]co[.]uk/w/l5fz[.]php |
| Online offers Branded pharmacueticals |
http://host[.]iceskatemag[.]co[.]uk/w/lztg[.]php |
When we visited these links they redirect to a counterfeit pill website featuring pain and anxiety medications such as Xanax, Tramadol, Ambien, Phentermine, and more. A depiction of the pill website with affiliate id is shown below.
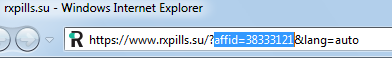 |
| Fig. 9: Redirect to a pill website with aff id |
When we tried to analyze these weblinks individually, they contained a list of php under the ‘w’ directory. Last, when tree walked just to the domain it led to a dating/porn website.
Inbound Spam
As can be seen in the Figure 3, there is a significant amount of inbound traffic that seems to be different spam messages redirected through our machine. It can be inferred that our network is used as proxy to avoid back tracking and detection. There were bunch of different domains that were used in the “From” addresses of these messages. An example of one such message is:
From: Walmart
Reply-To: newsletters@walmart.com
To: Grazielle
Subject: =?UTF-8?Q?Huge_Clearance_savings_you_can=E2=80=99t_miss?=
The capture contained different messages from all the following domains mentioned below:
aggadi.com.br
aol.com
belissimacosmeticos.com.br
catcorlando.com
citrosuco.com.br
connect.match.com
uspoloassn.com
newsletter.coastalscents.com
email.modait.com.br
facebookmail.com
id.apple.com
itmae.com.br
limecrimemakeup.com
offers.dominos.com
pcpitstopmail.com
photojojo.com
pof.com
sigmabeauty.com
submamails.com
twitter.com
walmart.com
Credential Exchange
TrickBot displays a similar characteristic to the
Kelihos Botnet , in a sense that it logs in to the mail server with the stolen credentials before it starts to send spam. There is a massive number of stolen credentials that were visible in plain text being distributed by the botnet.
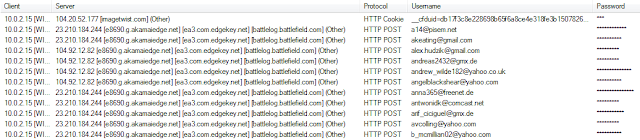 |
| Fig. 10: Stolen Credentials reconstructed in Network Miner |
With these analysis, it is safe to assume that TrickBot is extremely tricky!! Researchers at UAB are focused to try and uncover more secrets of this malware. Will keep everyone posted with our new findings!!
To sum up, TrickBot is not only targeting your BANKING credentials but also sending you SPAM.