How UK SMBs Can Prepare for the 5G Rollout
The UK government wants to extend 5G coverage to all populated areas of the country by 2030. Learn how your businesses can take full advantage. Continue reading How UK SMBs Can Prepare for the 5G Rollout
Collaborate Disseminate
The UK government wants to extend 5G coverage to all populated areas of the country by 2030. Learn how your businesses can take full advantage. Continue reading How UK SMBs Can Prepare for the 5G Rollout
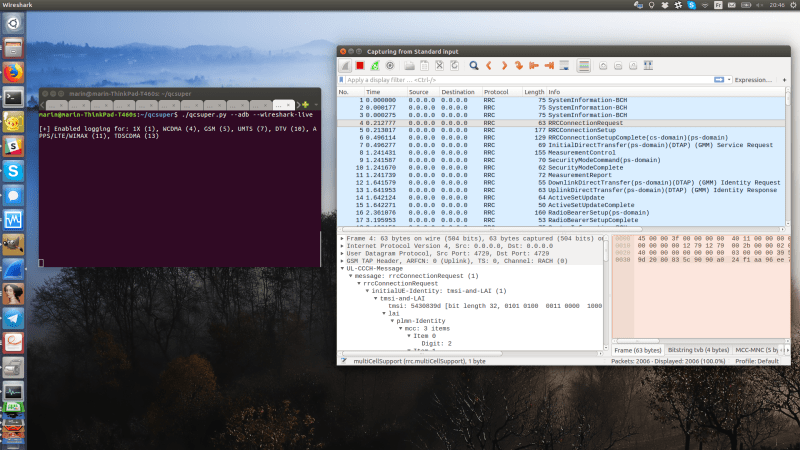
If your thought repurposing DVB-T dongles for generic software defined radio (SDR) use was cool, wait until you see QCSuper, a project that re-purposes phones and modems to capture raw …read more Continue reading Turn Your Qualcomm Phone Or Modem Into Cellular Sniffer
From artificial intelligence to 5G, 2024 could be a pivotal year for the tech industry and workers in the U.K. Continue reading UK Tech Trends & Predictions for 2024: AI Boosts Productivity, Hiring Increases, Fintech Matures, More 5G Rollouts

Since the very early 1990s, we have become used to ubiquitous digital mobile phone coverage for both voice and data. Such has been their success that they have for many …read more Continue reading 2G Or Not 2G, That Is The Question
Australia’s telcos are finally shutting down the 3G network. However, many critical services in security, healthcare and manufacturing continue to rely on the technology. Continue reading Window Closing for Australian Businesses to Upgrade From 3G
My question is Will enabling 4 only mode in a smartphone, prevent hackers from downgrading your connection to 3g/2g through fake towers.
Will using a Wpa3 router with VPN tethering function to share a 3g modem network protect someone from the vulnerabilities in a 3g network?
I know there are 4g and 5g, I just want to know how much is possible to build securely on an insecur… Continue reading Assuming 3g network is vulnerable, will it be also vulnerable if I tether it using a VPN router? [closed]
ETSI TS 135 206 defines the specification of MILENAGE algorithm which is an authentication algorithm for mobile networks.
It defines ‘OPc’ as below:
a 128-bit value derived from OP and K and used within the computation
of the functions.
… Continue reading How to calculate Millenage OPc value while OP stored in HSM?
You’ve got a machine hooked up to the Internet via a shiny new cellular modem, which you plan to administer remotely. You do a quick check on the external IP, and try and log in from another PC. Try as …read more
Continue reading Basics Of Remote Cellular Access: Connecting Via VPN
Some VPN providers offer to encrypt mobile data. This goes beyond the typical Wifi hotspot mitigation paradigm.
So what exactly are the benefits of VPN over mobile data? What threat models can this mitigate? Does this depend on the protoco… Continue reading What are the threat models that using a VPN for mobile data can mitigate?