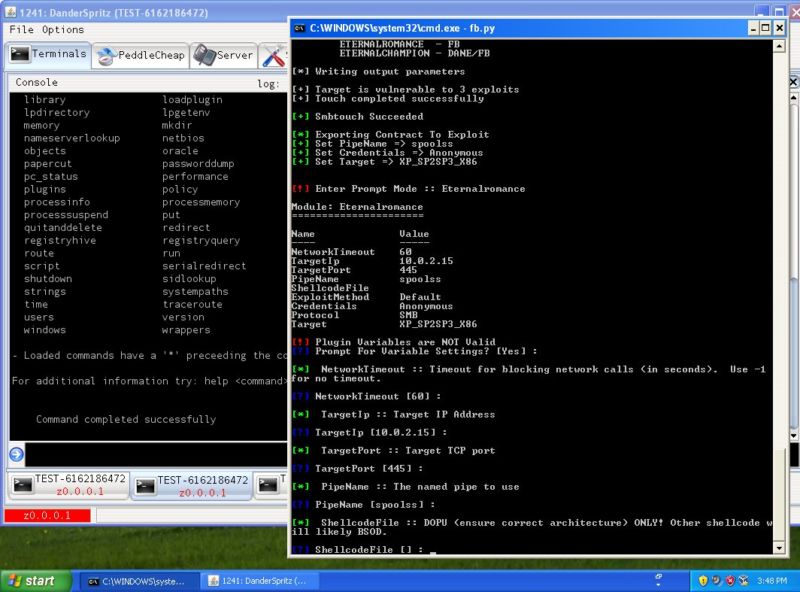
Enlarge / A computer screen displaying Eternalromance, one of the hacking tools dumped Friday by Shadow Brokers. (credit: Matthew Hickey)
Update:F-Secure has now retracted the claim the component completed in February used the NSA exploits. The retraction kills the premise this story. The headline has been changed, but the remainder of this now incorrect story is being preserved.
The people behind Tuesday’s massive malware outbreak had access to two National Security Agency-developed exploits several weeks before they were published on the Internet, according to evidence unearthed by researchers from antivirus F-Secure.
EternalBlue and EternalRomance, as the two exploits were codenamed, were two of more than a dozen hacking tools leaked on April 14 by an as-yet unknown group calling itself the Shadow Brokers. Almost immediately, blackhat and grayhat hackers used EternalBlue to compromise large numbers of computers running out-of-date versions of Microsoft Windows. Within a week or two, blackhats started using EternalBlue to install cryptomining malware. No one really noticed until the outbreak of the WCry ransomware worm on May 12, which infected an estimated 727,000 computers in 90 countries.