Enlarge (credit: AlienVault)
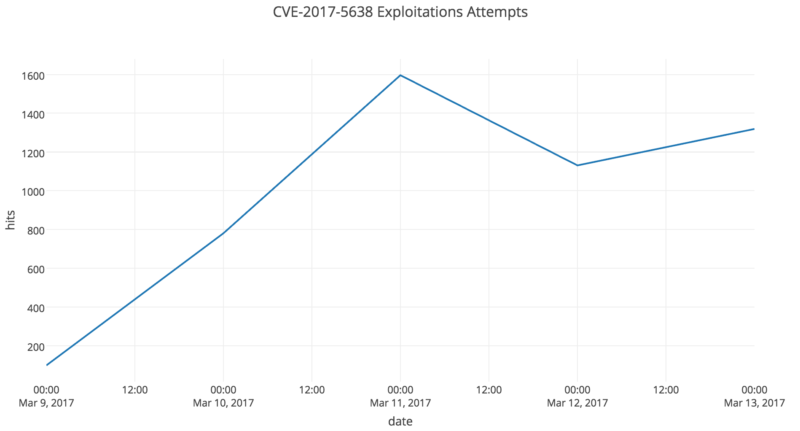
Eight days after developers patched a critical flaw in the Apache Struts Web application framework, there has been no let-up in the volley of attacks attempting to exploit the vulnerability, which affects a disproportionate number of high-impact websites, a security researcher said Tuesday.
As of Tuesday morning, 503 unique IP addresses were attempting to exploit the code execution bug, Jaime Blasco, chief scientist with security firm AlienVault Labs, told Ars. Based on the addresses, the attack origins were most concentrated in China (300 unique IPs), followed by the US (92), Taiwan (71), Hong Kong (15), the Netherlands (9), Russia (4), Canada (3), Italy (3), the UK, (3), and Indonesia (3). In an attempt to go undetected, the attackers in many cases have tweaked the two exploits that were being widely used in last week’s wave. AlienVault has responded by updating the signatures it uses to detect the attacks.
The five-year-old vulnerability resides in Web applications that were developed using a buggy version of Apache Struts. In many cases, the use of a single such app allows attackers to inject commands of their choice into the Web server hosting it. Like the attacks seen last week, the exploits are being used to infect vulnerable servers with a wide variety of malware.