
Enlarge (credit: Ron Amadeo)
Google has shut down a “high-severity” exploit in its Nexus 6 and 6P phones which gave attackers with USB access the opportunity to take over the onboard modem during boot-up—allowing them to listen in on phonecalls, or intercept mobile data packets.
The vulnerability was part of a cluster of security holes found by security researchers at IBM’s X-Force all related to a flaw—tagged CVE-2016-8467—in the phones’ bootmode, which uses malware-infected PCs and malicious power chargers to access hidden USB interfaces. Patches were rolled out before the vulnerabilities were made public, in November for the Nexus 6, and January for the 6P.
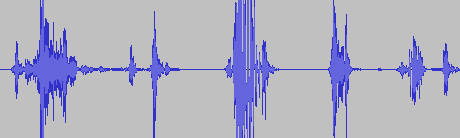
The waveform from a successfully intercepted phone call. (credit: IBM)
The exploit also allowed access to find the phone’s “exact GPS coordinates with detailed satellite information, place phone calls, steal call information, and access or change nonvolatile items or the EFS partition.”