Enlarge / From an upcoming paper laying out a new attack against 64-bit block ciphers used by HTTPS and OpenVPN. (credit: Karthikeyan Bhargavan and Gaëtan Leurent)
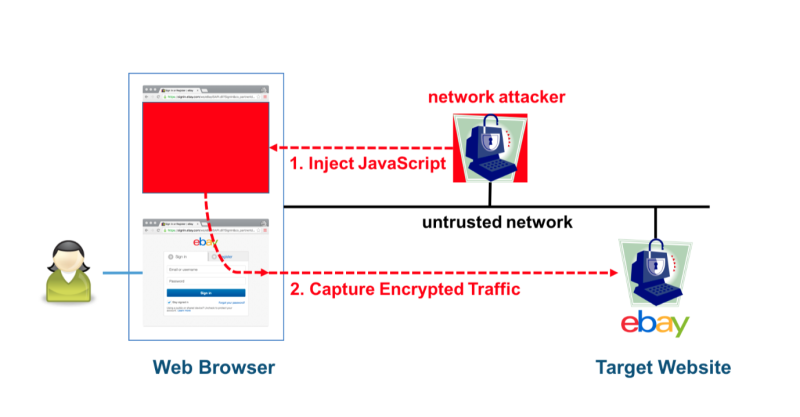
Researchers have devised a new attack that can decrypt secret session cookies from about 1 percent of the Internet’s HTTPS traffic and could affect about 600 of the Internet’s most visited sites, including nasdaq.com, walmart.com, match.com, and ebay.in.
The attack isn’t particularly easy to carry out because it requires an attacker to have the ability to monitor traffic passing between the end user and one of the vulnerable websites and to also control JavaScript on a webpage loaded by the user’s browser. The latter must be done either by actively manipulating an HTTP response on the wire or by hosting a malicious website that the user is tricked into visiting. The JavaScript then spends the next 38 hours collecting about 785GB worth of data to decrypt the cookie, which allows the attacker to log into the visitor’s account from another browser. A related attack against OpenVPN requires 18 hours and 705GB of data to recover a 16-byte authentication token.
Impractical no more
Despite the difficulty in carrying out the attack, the researchers said it works in their laboratory and should be taken seriously. They are calling on developers to stop using legacy 64-bit block-ciphers. For transport layer security, the protocol websites use to create encrypted HTTPS connections, that means disabling the Triple DES symmetric key cipher, while for OpenVPN it requires retiring a symmetric key cipher known as Blowfish. Ciphers with larger block sizes, such as AES, are immune to the attack.