Where should vulnerabilities be fixed? Source or Sink? [closed]
Where should vulnerabilities be fixed? Source or Sink?
Continue reading Where should vulnerabilities be fixed? Source or Sink? [closed]
Collaborate Disseminate
Where should vulnerabilities be fixed? Source or Sink?
Continue reading Where should vulnerabilities be fixed? Source or Sink? [closed]
In the Cryptsetup Frequently Asked Questions page it says:
You are asked a passphrase of an existing key-slot first, before you can enter the passphrase for the new key-slot. Otherwise you could break the encryption by just adding a new k… Continue reading Bypass encryption by altering source code
Hackers who reportedly stole valuable source code from games company Electronic Arts did so by first infiltrating the company’s Slack, a representative for a group claiming credit for the attack told Motherboard. For just $10, the hackers purchased a cookie that allowed them to infiltrate the $5 billion company’s Slack. They then posed as an employee to convince at IT administrator to grant them authentification to get into the company’s corporate network. The EA hack, first reported by Motherboard, included some game source code and related tools. No player data was accessed in the breach and the company does not expect the hack to impact its games, EA said in a statement. EA did not immediately respond to an email asking for verification of the hackers’ claims that they leveraged Slack to carry out the operation. The attack highlights the vulnerabilities created by workplace communication technologies, which have skyrocketed in […]
The post Hackers reportedly used EA Games’ Slack to breach network, access source code appeared first on CyberScoop.
Continue reading Hackers reportedly used EA Games’ Slack to breach network, access source code
We are a small tech startup. Currently, we have the entire codebase hosted in a private GitHub repository. Is this a good solution going forward (as we’re planning to expand the team rapidly) or should we shift it to something more secure?… Continue reading How to secure my organisations codebase?
If one made software, but later needed others to work on the project, how to secure the software files and source code if one of the developers tried to share the source code with others or if someone split from the team and tried to do so… Continue reading Building software in group
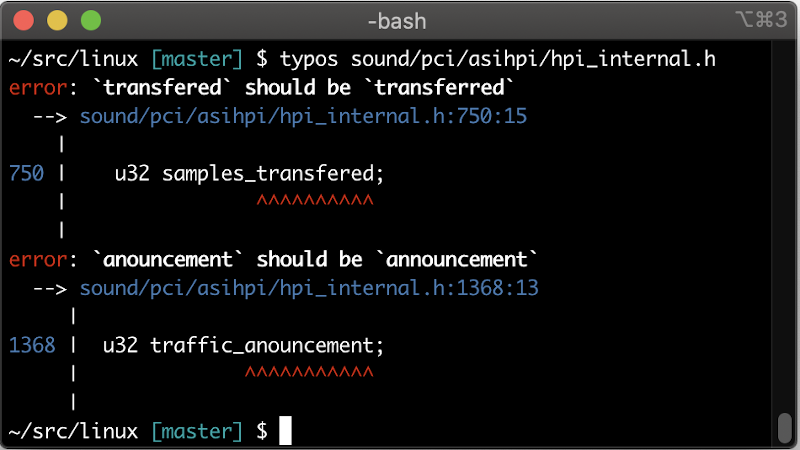
For most of us who didn’t do well in high school English class, spell checkers are a real game-changer. Sure, you can still swap a “to” and a “too,” but …read more Continue reading Spell Checking Your Programming from the Linux Command Line
By Habiba Rashid
The research team at vpnMentor, who discovered the data, believes that it belongs to Microsoft. Here’s what was leaked and what we know so far.
This is a post from HackRead.com Read the original post: Sensitive source codes exposed in … Continue reading Sensitive source codes exposed in Microsoft Azure Blob account leak
I would like to verify that users are running particular source code. Is there a way this could be achieved?
I want to verify that the original "algorithm" has been followed correctly if you will. What I need is for the user to s… Continue reading Is there a way to verify what code has been run? Maybe TEE?
Suppose you are going to mass manufacture custom circuit boards and would like the manufacturer to upload the device firmware onto these boards before shipping them out. What are some security systems/methodologies/features you would put i… Continue reading How to Prevent Copying of Device Source Code in Manufacturing
Let’s say HonestInc is super generous and provides the source code of its web application HonestApp on github. However, I’m extremely distrustful of them, and have doubts that their actual server is running the same source code as what is … Continue reading Is it possible to verify the source code of a web service? [duplicate]