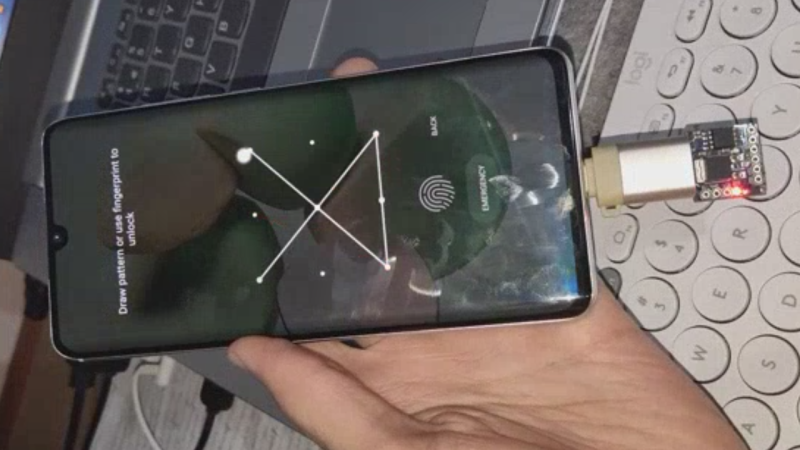
How widespread is mercenary spyware?
A targeted hunt on 2,500 mobile devices for indicators of compromise associated with mercenary spyware has revealed that its use is not as rare as one would hope. The results of the hunt Earlier this year, iVerify added a threat hunting feature to its … Continue reading How widespread is mercenary spyware?