Blast Chips with This BBQ Lighter Fault Injection Tool
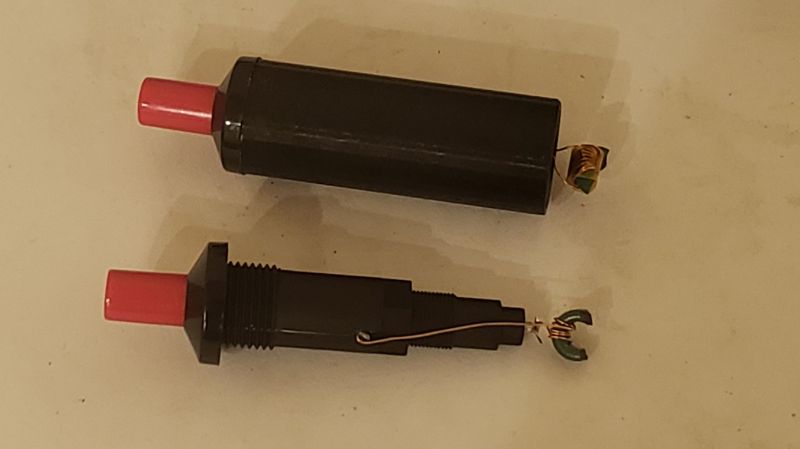
Looking to get into fault injection for your reverse engineering projects, but don’t have the cash to lay out for the necessary hardware? Fear not, for the tools to glitch …read more Continue reading Blast Chips with This BBQ Lighter Fault Injection Tool