Could Non-Planar Infill Improve The Strength Of Your 3D Prints?
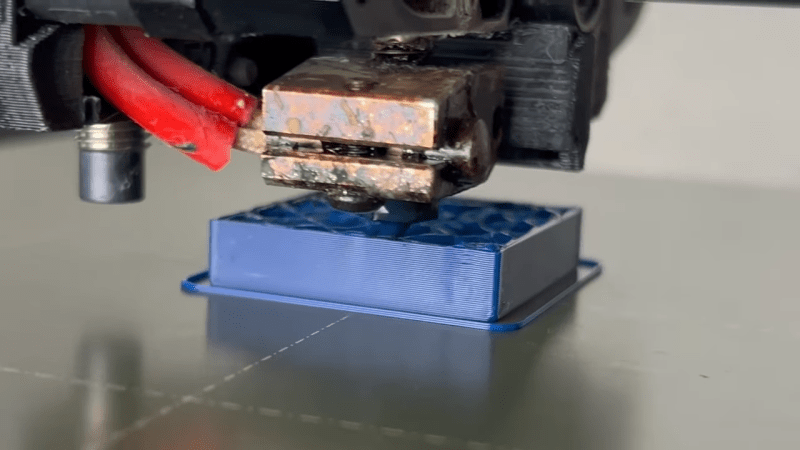
When you’re spitting out G-Code for a 3D print, you can pick all kinds of infill settings. You can choose the pattern, and the percentage… but the vast majority of …read more Continue reading Could Non-Planar Infill Improve The Strength Of Your 3D Prints?