Testing a proof of concept [closed]
Has anyone tested CVE-2017-0475.zip to get root? It is an elevation of priviledge proof of concept attack on Android recovery.
Collaborate Disseminate
Has anyone tested CVE-2017-0475.zip to get root? It is an elevation of priviledge proof of concept attack on Android recovery.
Has anyone tested CVE-2017-0475.zip to get root? It is an elevation of priviledge proof of concept attack on Android recovery.
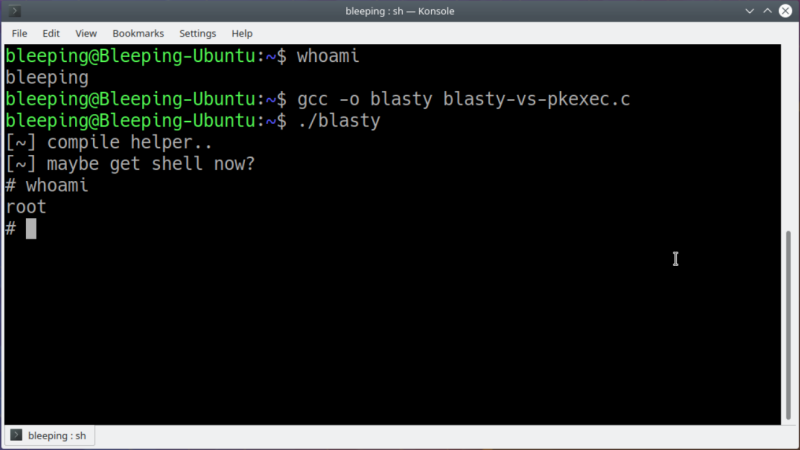
One of the major reasons behind choosing Linux as an operating system is that it’s much more secure than Windows. There are plenty of reasons for this including appropriate user …read more Continue reading Major Bug Grants Root for All Major Linux Distributions
Can anyone give my an example of how the CVE-2017-0475 exploit works.
Continue reading Can someone give an example of how CVE-2017-0475 is used in the wild? [closed]
I worry I might have viruses, malware, keyloggers, backdoor…etc. on my phone and need something powerful to scan my phone and remove them.
Perhaps something popular and commonly agreed upon in the power user community…like how xposed i… Continue reading What’s the best way to remove malware from a rooted Android 7.0? [closed]

It’s not a jailbreak, but [basti564]’s Oculess software nevertheless allows one the option to remove telemetry and account dependencies from Facebook’s Oculus Quest VR headsets. It is not normally possible …read more Continue reading Software Removes the Facebook from Facebook’s VR Headset (Mostly)
linux security and root access question….
I’m setting up a server that has a validator node running on it for a blockchain. I was trying to harden the security of my server. I set up ufw for all ports but those necessary for the node to … Continue reading Disable everything but a hidden command for root access
linux security and root access question….
I’m setting up a server that has a validator node running on it for a blockchain. I was trying to harden the security of my server. I set up ufw for all ports but those necessary for the node to … Continue reading Disable everything but a hidden command for root access
I need to have security certificates renewed soon on several RedHat servers. Will I need root access to install them?
Continue reading Do I need root access to install a certificate?
I have recently been assigned a new security fix for my Android App.
The Vulnerability Assessment and Penetration Testing (VAPT) team used Magisk and Magisk hide to bypass the Android root detection implementation.
The description given by… Continue reading Root detection can be bypassed using Magisk hide: how to mitigate?