Radicle: An Open-Source, Peer-to-Peer, GitHub Alternative
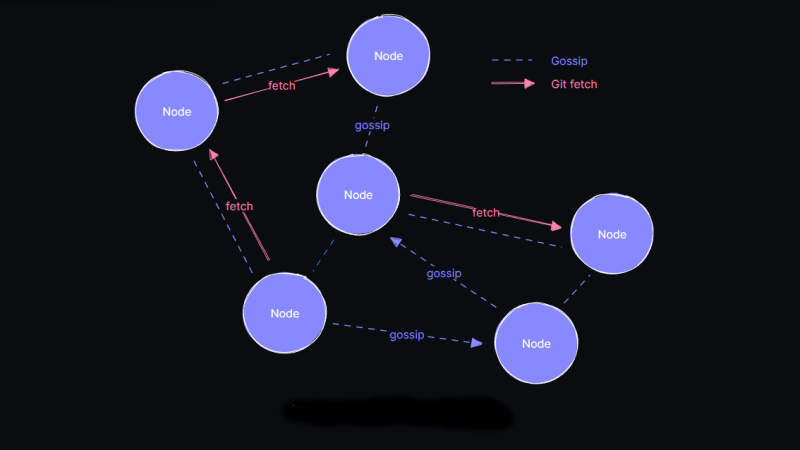
The actions of certain large social networks have recently highlighted how a small number of people possess significant power over the masses and how this power is sometimes misused. Consequently, …read more Continue reading Radicle: An Open-Source, Peer-to-Peer, GitHub Alternative
