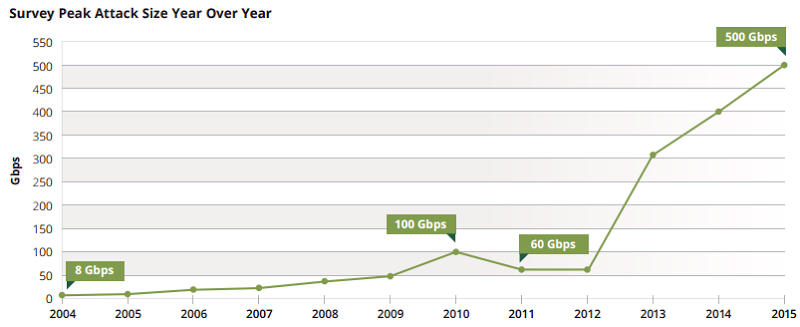
I’ve just launched my latest Pluralsight course titled Ethical Hacking, Denial of Service but before I explain what’s in it, let’s kick off with some trivia: DDoS attacks have increased massively in size in recent years:

This is from Arbor Networks’ latest Worldwide Infrastructure Security Report and that was current in October when the study was done. Now, it’s not so current:

By the time you read this, we may well be at 700 or 800 or who knows where because the trend is very consistently “up and to the right”, as they say. But it’s not just the scale of the attacks which is alarming, it’s the cost. We may think of a DDoS attack as being a simple temporary outage (or a peaceful protest, as some would like to see it), but have a look at how much Arbor found it actually costs organisations in their report:

So about two thirds of company take a hit of $30k an hour or more. 14% of them were seeing costs upwards of ten times that – $300k per hour because of DDoS!
But here’s the other crazy thing about this class of attack – it’s easy, it’s cheap and you don’t need any specific app flaws in order to seriously mess with a site. Here’s a perfect example of how easily DDoS is, go and check out this site (turn your speakers way up first!):

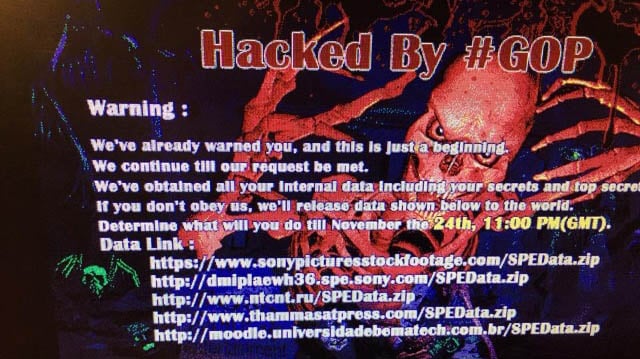
I’m not normally in the habit of linking through to malicious sites, but “booters” are so prevalent and easily accessible on the clear web that you’ll find them within minutes anyway if you want to. The crazy thing with the booters is the sheer prevalence of them and the ease with which they seem to be spun up. For example, the Lizard Squad service of late 2014 which proved to be rather effective at taking down the likes of Sony’s PSN and Microsoft’s Xbox Live. Even kids in their bedrooms are spinning up DDoS services these days:
Now to be clear, I’m not exactly sure how effective Christa’s service really is, but there’s something about DDoS that really appeals to kids. Part of it is likely that they’re just so easy to execute in an impactful way; not only are there many DDoS as a service offerings out there (DDoSaas?), they also don’t need any specific vulnerabilities in the target site in order to cause damage. No SQL injection or XSS or enumeration risks or anything like that, they merely need a site which can handle less traffic than they can send it.
DDoS has also become a favourite with this genre that we know as the hacktivist. For example, we’ve seen successful attacks based on philosophical differences such as #oppayback in the wake of PayPal and co refusing to accept donations to Wikileaks. The legalities of this action aside (and I’ll come back to that), you can understand the ire the hacktivists felt in the wake of PayPal’s decision. Likewise, there probably wasn’t a whole lot of sympathy when hactivists DDoS’d Scientology and I suspect next to zero sympathy when it was Westborough Baptist church being hit.
But the ease of this class of attack also makes for some pretty unreasonable action on behalf of adversaries. For example, just a couple of months ago Nissan was DDoS’d. Why? No, not because they build cars with security flaws, rather it was because of the whales. Hang on – what? This is not because Nissan is upholstering cars in whale skin or testing airbags on them or anything whacky like that, it’s because Nissan is Japanese and there remains “scientific research” there which involves harpooning them. (It’s unclear how scientific turning them into sushi is, but I digress.) The point is that Nissan themselves almost certainly have nothing to do with whaling yet they copped a rather effective DDoS there for a while.
Another reason DDoS attacks remain rampant particularly via hacktivists is that they frequently don’t believe there’ll be any recourse. I recently watched the We Are Legion documentary (not sensational, but worthwhile viewing IMHO), and it was interesting to see just how unaware so many of those involved in the aforementioned #oppayback attacks were. They gave no thought to the fact that what they were doing might be illegal and could have serious consequences. Being entirely objective about it, you can see how they might draw that conclusion; they’re sitting there in their bedrooms firing up a tool like LOIC (a favourite with hacktivists) and then just… going outside and playing. No seriously, here’s a tutorial by Anonymous that tells you to do just that:
Ok, this is funny for many reasons yet it does demonstrate how eager especially kids or young adults are to jump on the DDoS bandwagon. In the aforementioned documentary, many of those interviewed talked about how DDoS was just a form of protest, in fact even their lawyer was quite adamant they were just exercising their freedom of speech rights. The problem is though, when you’re costing an organisation thousands of dollars by the minute, you’re actually doing serious damage and with that comes serious consequences. A few years back I wrote What is LOIC and can I be arrested for DDoS’ing someone? because I was amazed at just how many people thought they couldn’t be arrested for it!
I could go on about DDoS because it’s a genuinely fascinating topic, but I do want to touch on the point of writing the post in the first place which is to launch my latest (and 21st) Pluralsight course titled Ethical Hacking, Denial of Service. This is now the 6th course in the Ethical Hacking series and I decided to break it down into four modules like so:
- Understanding Denial of Service Attacks: How this class of attack has grown so rapidly in recent years and the impact it’s having on organisations, as well as some really neat visualisation of attacks such as the Norse map.
- Attack Techniques: There’s a lot more to denial of service attacks than a bunch of people pointing LOIC at a site. SYN floods, ICMP and UDP attacks, DNS amplification and even the man on the side style of attack we saw against GitHub last year to name just a few.
- Tools and Services: Obviously I touch on LOIC (and it’s web-based counterpart JS LOIC) and I then delve into the operations of booters as mentioned above and the whole DDoSaaS class of offering. In fact I even do a walkthrough of one of these which gives some insight into just how polished these services have become.
- Defending Against Attacks: Given the course is aimed at your ethical class of professional, I naturally spend a bunch of time talking about how to limit the effectiveness of these attacks. It’s never foolproof, but there’s a lot that can be done to lessen the blow of an attack.
That’s it for DDoS, the course is now live and ready to be viewed – enjoy!
 Continue reading New Pluralsight course: Ethical Hacking, Denial of Service→
Continue reading New Pluralsight course: Ethical Hacking, Denial of Service→